 Tarantula Hawk numbers up in TX. If stung "just lie down and start screaming" http://www.wired.com/2015/07/absurd-creature-of-the-week-tarantula-hawk/ … via @WIRED
Tarantula Hawk numbers up in TX. If stung "just lie down and start screaming" http://www.wired.com/2015/07/absurd-creature-of-the-week-tarantula-hawk/ … via @WIRED
Number 1 and Benford’s Law - Numberphile (by numberphile)
I’d heard of Benford’s Law before but it sounded totally counter intuitive to me. This video does a good job explaining why one shows up as the leading digit in sets of random numbers that span large ranges.
In JavaScript numbers are 64bit floating point numbers which have 53 bits of mantissa. That means you can accurately represent [-2^53, 2^53] as integers in JavaScript. Aka [-9007199254740992, 9007199254740992].
def nextServerCallback(self, data):
parsed_data = json.loads(data)
# Chunk was wrong!
if not parsed_data['success']:
# Defend against timing attacks
remaining_time = self.expectedRemainingTime()
self.log_info('Going to wait %s seconds before responding' %
remaining_time)
reactor.callLater(remaining_time, self.sendResult, False)
return
self.checkNext()An analysis of leaked PIN numbers.
… nearly 11% of the 3.4 million passwords are 1234 !!!
A series of videos with math profs explaining a specific number (or interesting topic with a contrived connection to a particular number)
The conversation surrounding how to liberate HBO from its cable partners and create the entertainment utopia viewers have long desired has been fascinating.
The resulting analyses of the numbers has pretty much shown that the amount people are willing to pay is not nearly enough to…
perl -lne ‘(1x$_) =~ /^1?$|^(11+?)\1+$/ || print “$_ is prime”’
I'm making a switch from the IE team to the Windows team where I'll be working on the next version of Windows. As a going away surprise Jen and Nick added me to my gallery of Bill Gates (discussed previously). Here's a close up of the photoshopped cover.
In honor of Google Chrome's recent v2 release and because I read they don't make too big a deal about version numbers, I thought to create a graph of browser major version numbers over time.
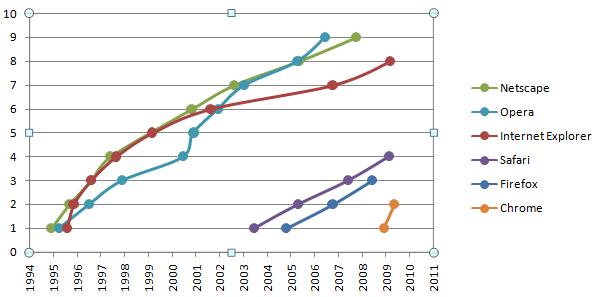
Yeah that's not too useful of a graph. I got the release dates from Wikipedia of course.
As you can see from the graph, Netscape and Opera are leading all other browsers in terms of major version number. The other browsers really need to get on that.
Windows allows for application protocols in which, through the registry, you specify a URL scheme and a command line to have that URL passed to your application. Its an easy way to hook a webbrowser up to your application. Anyone can read the doc above and then walk through the registry and pick out the application protocols but just from that info you can't tell what the application expects these URLs to look like. I did a bit of research on some of the application protocols I've seen which is listed below. Good places to look for information on URI schemes: Wikipedia URI scheme, and ESW Wiki UriSchemes.
| Scheme | Name | Notes |
|---|---|---|
| search-ms | Windows Search Protocol |
The search-ms application protocol is a convention for querying the Windows Search index. The protocol enables applications, like Microsoft Windows Explorer, to query the index with
parameter-value arguments, including property arguments, previously saved searches, Advanced Query Syntax, Natural Query Syntax, and language code identifiers (LCIDs) for both the Indexer and
the query itself. See the MSDN docs for search-ms for more info. Example: search-ms:query=food |
| Explorer.AssocProtocol.search-ms | ||
| OneNote | OneNote Protocol |
From the OneNote help: /hyperlink "pagetarget" - Starts OneNote and opens the page specified by the pagetarget parameter. To obtain the hyperlink for any page in a OneNote
notebook, right-click its page tab and then click Copy Hyperlink to this Page.Example: onenote:///\\GUMMO\Users\davris\Documents\OneNote%20Notebooks\OneNote%202007%20Guide\Getting%20Started%20with%20OneNote.one#section-id={692F45F5-A42A-415B-8C0D-39A10E88A30F}&end |
| callto | Callto Protocol |
ESW Wiki Info on callto Skype callto info NetMeeting callto info Example: callto://+12125551234 |
| itpc | iTunes Podcast |
Tells iTunes to subscribe to an indicated podcast. iTunes documentation. C:\Program Files\iTunes\iTunes.exe /url "%1" Example: itpc:http://www.npr.org/rss/podcast.php?id=35 |
| iTunes.AssocProtocol.itpc | ||
| pcast | ||
| iTunes.AssocProtocol.pcast | ||
| Magnet | Magnet URI | Magnet URL scheme described by Wikipedia. Magnet URLs identify a resource by a hash of that resource so that when used in P2P scenarios no central authority is necessary to create URIs for a resource. |
| mailto | Mail Protocol |
RFC 2368 - Mailto URL Scheme. Mailto Syntax Opens mail programs with new message with some parameters filled in, such as the to, from, subject, and body. Example: mailto:?to=david.risney@gmail.com&subject=test&body=Test of mailto syntax |
| WindowsMail.Url.Mailto | ||
| MMS | mms Protocol |
MSDN describes associated protocols. Wikipedia describes MMS. "C:\Program Files\Windows Media Player\wmplayer.exe" "%L" Also appears to be related to MMS cellphone messages: MMS IETF Draft. |
| WMP11.AssocProtocol.MMS | ||
| secondlife | [SecondLife] |
Opens SecondLife to the specified location, user, etc. SecondLife Wiki description of the URL scheme. "C:\Program Files\SecondLife\SecondLife.exe" -set SystemLanguage en-us -url "%1" Example: secondlife://ahern/128/128/128 |
| skype | Skype Protocol |
Open Skype to call a user or phone number. Skype's documentation Wikipedia summary of skype URL scheme "C:\Program Files\Skype\Phone\Skype.exe" "/uri:%l" Example: skype:+14035551111?call |
| skype-plugin | Skype Plugin Protocol Handler |
Something to do with adding plugins to skype? Maybe. "C:\Program Files\Skype\Plugin Manager\skypePM.exe" "/uri:%1" |
| svn | SVN Protocol |
Opens TortoiseSVN to browse the repository URL specified in the URL. C:\Program Files\TortoiseSVN\bin\TortoiseProc.exe /command:repobrowser /path:"%1" |
| svn+ssh | ||
| tsvn | ||
| webcal | Webcal Protocol |
Wikipedia describes webcal URL scheme. Webcal URL scheme description. A URL that starts with webcal:// points to an Internet location that contains a calendar in iCalendar format. "C:\Program Files\Windows Calendar\wincal.exe" /webcal "%1" Example: webcal://www.lightstalkers.org/LS.ics |
| WindowsCalendar.UrlWebcal.1 | ||
| zune | Zune Protocol |
Provides access to some Zune operations such as podcast subscription (via Zune Insider). "c:\Program Files\Zune\Zune.exe" -link:"%1" Example: zune://subscribe/?name=http://feeds.feedburner.com/wallstrip. |
| feed | Outlook Add RSS Feed |
Identify a resource that is a feed such as Atom or RSS. Implemented by Outlook to add the indicated feed to Outlook. Feed URI scheme pre-draft document "C:\PROGRA~2\MICROS~1\Office12\OUTLOOK.EXE" /share "%1" |
| im | IM Protocol |
RFC 3860 IM URI scheme description Like mailto but for instant messaging clients. Registered by Office Communicator but I was unable to get it to work as described in RFC 3860. "C:\Program Files (x86)\Microsoft Office Communicator\Communicator.exe" "%1" |
| tel | Tel Protocol |
RFC 5341 - tel URI scheme IANA assignment RFC 3966 - tel URI scheme description Call phone numbers via the tel URI scheme. Implemented by Office Communicator. "C:\Program Files (x86)\Microsoft Office Communicator\Communicator.exe" "%1" |
 The names in the following anecdote have been changed. Except for my name
(I'm Dave).
The names in the following anecdote have been changed. Except for my name
(I'm Dave).
I got a new laptop a while back. I had it in my office and Tim came in to ask me something but paused when he saw my laptop. "Oh, is this one of those new touch screen laptops?" he asked, the whole time moving his hand towards my laptop and punctuating his sentence by pressing his finger to the screen. "No" I responded.
Walking down a hallway I heard Winston, one of our managers, say, "Hey Tim!" Winston catches up to me and asks, "Are you almost done with the XYZ bug?" I realized Winston was talking to me and got my name wrong but I figured I'll ignore it and perhaps he'll realize his mistake. Winston continued "I just talked with some people who say they're blocked and waiting for Tim to finish the XYZ bug." "Dave" I said helpfully attempting to diplomatically correct Winston since he apparently hadn't realized his error. "No, it was Jeremy and Bill." Winston said naming the people he had talked to who were waiting for me to fix the XYZ bug. At this point I decided it would be easier to just answer his question and end the conversation than to get into this whole thing. As far as I know, Winston has not gotten my name wrong at any other time.
In my Intro to Algorithms course in college the Fibonacci sequence was used as the example algorithm to which various types of algorithm creation methods were applied. As the course went on we made
better and better performing algorithms to find the nth Fibonacci number. In another course we were told about a matrix that when multiplied successively produced Fibonacci numbers. In my linear
algebra courses I realized I could diagonalize the matrix to find a non-recursive Fibonacci function. To my surprise this worked and I
found a function.
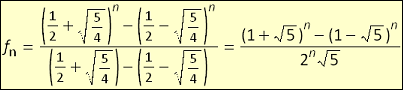
Looking online I found that of course this same function was already well known. Mostly I was irritated that after all the
algorithms we created for faster and faster Fibonacci functions we were never told about a constant time function like this.
I recently found my paper depicting this and thought it would be a good thing to use to try out MathML, a markup language for displaying math. I went to the MathML implementations page and installed a plugin for IE to display MathML and then began writing up my paper in MathML. I wrote the MathML by hand and must say that's not how its intended to be created. The language is very verbose and it took me a long time to get the page of equations transcribed.
MathML has presentation elements and content elements that can be used separately or together. I stuck to content elements and while it looked great in IE with my extension when I tried it in FireFox which has builtin MathML support it didn't render. As it turns out FireFox doesn't support MathML content elements. I had already finished creating this page by hand and wasn't about to switch to content elements. Also, in order to get IE to render a MathML document, the document needs directives at the top for specific IE extensions which is a pain. Thankfully, the W3C has a MathML cross platform stylesheet. You just include this XSL at the top of your XHTML page and it turns content elements into appropriate presentation elements, and inserts all the known IE extension goo required for you. So now my page can look lovely and all the ickiness to get it to render is contained in the W3C's XSL.