2008 Jun 18, 12:44Bruce Schneier writes about LifeLock for which you've probably seen the comercials of the CEO parading around his SSN. I was wondering what LifeLock actually did.
 bruce-schneier identity fraud credit article wired security privacy lifelock
bruce-schneier identity fraud credit article wired security privacy lifelock 2008 Jun 10, 3:34ArsTechnica has an interview with FCC commissioner Jonathan Adelstein. Talks about policy in general with an eye towards net neutrality.
 interview fcc jonathan-adelstein arstechnica article
interview fcc jonathan-adelstein arstechnica article 2008 Jun 10, 3:10Interview with guy from "the Seasteading Institute, the brainchild of two Silicon Valley software developers, aims to develop self-sufficient deep-sea platforms that would empower individuals to
break free of the cozy cartel of 190-odd world governments a
 community politics seasteading society article arstechnica
community politics seasteading society article arstechnica 2008 May 30, 1:36Killbits: "This article describes how to stop an ActiveX control from running in Microsoft Internet Explorer and in Windows Internet Explorer. You can do this by modifying the data value of the
Compatibility Flags DWORD value for the Class identifier (CLS
 security ie killbit msdn microsoft windows browser reference
security ie killbit msdn microsoft windows browser reference 2008 May 30, 10:52'"Richard Feynman reporting for duty. OK, boss, what's my assignment?" The assembled group of not-quite-graduated MIT students was astounded.... So we sent him out to buy some office supplies.'
 history richard-feynman programming computer article essay technology physics science via:swannman
history richard-feynman programming computer article essay technology physics science via:swannman 2008 May 30, 10:02'What happened to me (and what happens to thousands of others each month) is known as "cramming." The [FTC] calls this "the practice of placing unauthorized, misleading, or deceptive charges on your
telephone bill...'
 article cramming security marketing
article cramming security marketing 2008 May 18, 6:45
While re-reading Cryptonomicon I thought
about what kind of information I'm leaking by posting links on Delicious. At work I don't post any Intranet websites for fear of revealing anything but I wondered if not posting would reveal
anything. For instance, if I'm particularly busy at work might I post less indicating something about the state of the things I work on? I got an archive of my Delicious posts via the Delicious API
and then ran it through a tool I made to create a couple of tables which I've graphed on Many Eyes
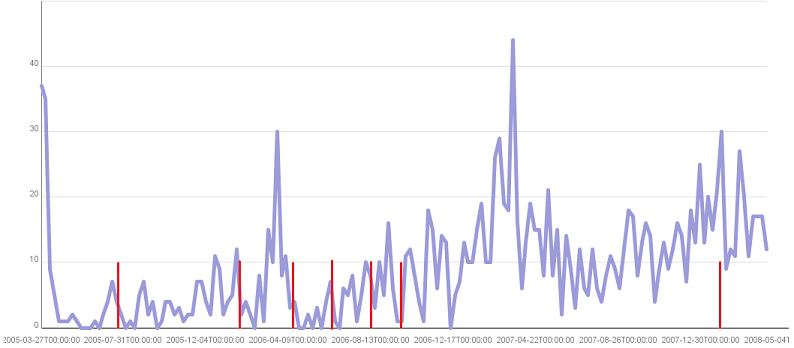
I've graphed my posts per week and with red lines I've marked IE7 and IE8 releases as stated by Wikipedia. As you can see, there doesn't seem to be much of a pattern so I suppose my concerns
we're unfounded. I use it for both work and non-work purposes and my use of Delicious isn't that consistent so I don't think it would be easy to find a pattern like I was thinking about. Perhaps if
many people from my project used Delicious and that data could be compared together it might be easier.


For fun I looked at my
posts per day of week which starts off strong on Mondays and decreases as the
week goes on, and my
posts per hour of day. It looks like I mostly post around lunch and on the extremes I've
only posted very late at night twice at 4am:
converting media for the Zune, and
Penn's archive of articles. In the morning at 7am I've posted only once:
document
introducing SGML.
 manyeyes graph cryptonomicon delicious
manyeyes graph cryptonomicon delicious 2008 May 5, 11:42Video of "Mike Klucher talks about building XNA Framework games for the Zune and shows the soon-to-be-released CTP that enables developers to build Zune projects, adds a new menu on your Zune for
games, and also enables device debugging directly from Visu
 zune xbox videogame development microsoft blog article video
zune xbox videogame development microsoft blog article video 2008 Apr 30, 10:48"anything that gets invented after you're thirty is against the natural order of things and the beginning of the end of civilisation as we know it until it's been around for about ten years when it
gradually turns out to be alright really."
 via:ethan_t_hein history internet douglas-adams article essay
via:ethan_t_hein history internet douglas-adams article essay 2008 Apr 28, 12:55Clay Shirky talks about the surplus of thought that TV occupies.
 article clay-shirky culture internet tv technology collaboration community history
article clay-shirky culture internet tv technology collaboration community history 2008 Apr 22, 4:33Reaction to Phrack's howto on GPS jammer. Sounds like the article wants to make it into a bigger issue than it is: "Information in the article that appears in the current issue of the online hacker
magazine Phrack potentially puts at risk GPS devices use
 gps gps-jamming phrack government
gps gps-jamming phrack government 2008 Apr 21, 5:03Hyper-V is a cool virtualization software product (apparently) that I need to look into.
 hyper-v microsoft download blog article virtualization tool
hyper-v microsoft download blog article virtualization tool 2008 Apr 21, 12:05ISPs show ads for unreigstered domains including subdomains which malicious folk use to XSS. Oops.
 article security internet web xss advertising
article security internet web xss advertising 2008 Apr 18, 12:58"I found myself in possession of the "Infocom Drive" - a complete backup of Infocom's shared network drive from 1989." He posts emails from that backup w/o consulting those involved who show up for
luke warm debate in the comments.
 if interactive-fiction infocom hhgttg history scifi videogame article
if interactive-fiction infocom hhgttg history scifi videogame article 2008 Apr 11, 3:22Forbe's ranks the 15 richest fictional characters: "The characters that make up this year's edition of the Forbes Fictional 15, our annual listing of fiction's richest, boast an aggregate net worth
of $137 billion."
 forbes humor fiction article comic
forbes humor fiction article comic 2008 Apr 10, 8:14"In this post, I've given five useful examples of URL rewriting using .htacess."
 htaccess apache linux reference uri url example blog article
htaccess apache linux reference uri url example blog article 2008 Apr 9, 8:26"I'm going to cover three basic techniques for incorporating some simple data visualization into standards-based navigation patterns."
 css web visualization chart html via:swannman
css web visualization chart html via:swannman 2008 Apr 9, 2:36History of Enigma in WW2: "One particular German code clerk continually used his girlfriend's name, Cillie, for his messages, and so these easy-to-guess indicators became known as "Cillies.""
 history encryption cryptography article security nsa enigma
history encryption cryptography article security nsa enigma 2008 Apr 8, 5:41Biology site makes activity to resolve their URNs: "In this case we decided to see how we could easily highlight a LSID and quickly get related information from its Authority."
 activity ie8 urn uri blog article biology via:benny
activity ie8 urn uri blog article biology via:benny 2008 Apr 8, 1:52"The Culture War: How new media keeps corrupting our children." Article snippets condemning novels in 1700s, the Waltz 1800s, Movies, Telephone, etc etc. for corrupting the youth
 article wired videogames culture youth media censorship comic politics history humor
article wired videogames culture youth media censorship comic politics history humor


