 Amazon doesn't say how it determines friendship because that exposes work around
or because we would be creeped out? https://twitter.com/niftyc/status/618275252049608704 …
Amazon doesn't say how it determines friendship because that exposes work around
or because we would be creeped out? https://twitter.com/niftyc/status/618275252049608704 …
 The NSA does not have "an absolute right to gain access to every way in which two
people may choose to communicate." http://arstechnica.com/tech-policy/2015/04/nsa-dreams-of-smartphones-with-split-crypto-keys-protecting-user-data/ …
The NSA does not have "an absolute right to gain access to every way in which two
people may choose to communicate." http://arstechnica.com/tech-policy/2015/04/nsa-dreams-of-smartphones-with-split-crypto-keys-protecting-user-data/ …
 Naming is important: in Rails you can output raw unescaped HTML with
.safe_html - in React a similar API is called dangerouslySetInnerHTML
Naming is important: in Rails you can output raw unescaped HTML with
.safe_html - in React a similar API is called dangerouslySetInnerHTML
 RE: anti @WordPress "There are 2 types of
programming languages: the ones ppl complain about and the ones nobody uses." -Bjarne Stroustrop
RE: anti @WordPress "There are 2 types of
programming languages: the ones ppl complain about and the ones nobody uses." -Bjarne Stroustrop
 Magazines are trying to create new categories of “super-subscribers” http://nie.mn/1DUg1f8
Magazines are trying to create new categories of “super-subscribers” http://nie.mn/1DUg1f8
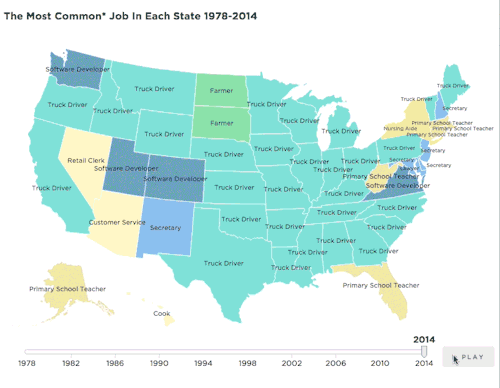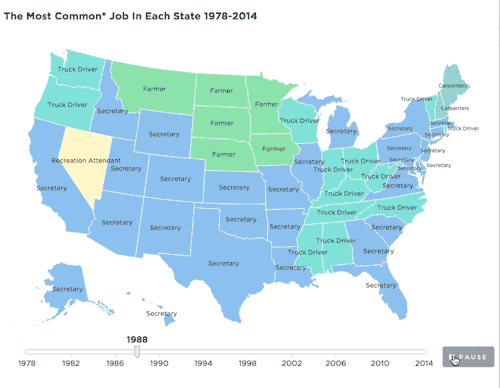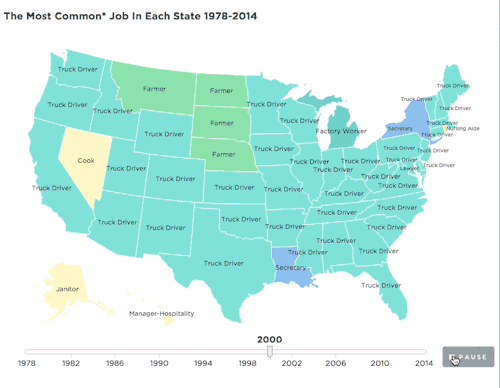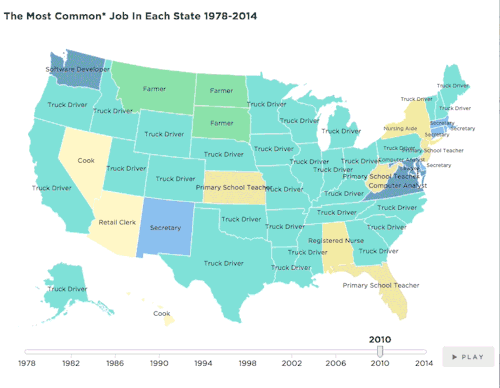
npr:
The jobs picture has changed profoundly since the 1970s. This map shows how that has played out across the country.
Map: The Most Common Job In Every State
Source: IPUMS-CPS/ University Of Minnesota
Credit: Quoctrung Bui/NPR

npr:
The jobs picture has changed profoundly since the 1970s. This map shows how that has played out across the country.
Map: The Most Common Job In Every State
Source: IPUMS-CPS/ University Of Minnesota
Credit: Quoctrung Bui/NPR
On exploiting security issues in botnet C&C software:
Hackers “are learning that it’s not so easy to write secure code,” Toro says. “Most of us in the business of securing our applications and systems know that bulletproofing software is an extremely expensive and exhaustive undertaking. Malware creators who have to look to their own defences would have to slow down the production of new attacks.”
FYI, if you want to know what it looks like when you hack a hacker, look no further than the seminal 1995 film Hackers.

MotherJones - Meet the people behind the Wayback Machine, one of our favorite things about the internet
YouTube - Dead Man’s Bones (Dance)
Nathan Barnatt has some great videos
A reminder that those Doritos you love are trash:
Shortly after Disneyland opened in 1955, the founder of Frito-Lay got permission from Walt Disney to open a restaurant in Frontierland with a Mexican-ish theme. “Casa de Fritos” was, unsurprisingly, all about the Fritos. Customers got free Fritos, and Fritos were incorporated into many of the dishes. Fritos were dispensed by an animatronic vending machine that featured the terrifying “Frito Kid”asking his assistant “Klondike” to bring the bag up from a mineshaft. I guess the conceit is that Fritos were mined by Forty-Niners?
Casa de Fritos contracted their tortilla production to a company called Alex Foods. One of the salesmen from Alex Foods, making a delivery to Casa de Fritos, noticed stale tortillas in the garbage and gave the cook a little tip: fry them and sell them as chips instead of throwing them away. Casa de Fritos began making these fried, seasoned chips to enormous success, but didn’t report this new menu item to the Frito-Lay company.
Eventually Frito-Lay found out what they were doing with the chips, packaged them, and sold them by the truckload. See, dumpster diving works out sometimes!
Clearly the one JS feature we all agree on is ubiquity.
After some experimentation, I discovered that it’s possible to add type safety to JavaScript objects [via ES6 proxies] with just a few lines of code.
Adds the yield keyword enabling you to write JS code that sort of looks like C# await.
Overview
First-class coroutines, represented as objects encapsulating suspended execution contexts (i.e., function activations). Prior art: Python, Icon, Lua, Scheme, Smalltalk.
You don’t use the same password over and over right? Let’s be honest this is the day and age of the hacker. Eclectic Method brings you “Hackers” , Hollywood’s celebration of basement dwelling 128 bit encryption masters. They’ll shut down before you can trace them, hack into the mainframe…
Hack the planet!
This is essentially an AV exploit against Super Mario World that results in running the end game code. Watch the video. “…there’s a glitch that’s been known for a while, where Yoshi can end up in the “I have an item in my mouth” state, but not actually have an item in his mouth. When he spits out this nothingness, the game crashes. …That address did not contain code, and so the system crashed. But wait a second. What if, by some sheer coincidence, that address did contain code? The specific address dropped him in somewhere amongst various data for the game’s internal random number generator, and the random number generator can be manipulated in a TAS. Could the game be coerced into running arbitrary code?…”
Zelda Starring Zelda (by Kenna W)
Original NES Legend of Zelda ROM modified to swap Zelda and Link: play as Zelda saving Link.