Waxy roundup of DMCA takedown process stupidity.
“So the Scripps TV broadcasts are indexed by YouTube, and the Content ID robots do the rest. And because Content ID disputes are judged by the copyright holder, complaints are routinely ignored or denied.”
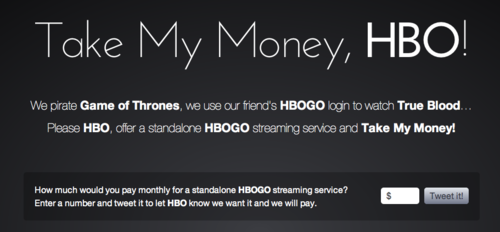
The conversation surrounding how to liberate HBO from its cable partners and create the entertainment utopia viewers have long desired has been fascinating.
The resulting analyses of the numbers has pretty much shown that the amount people are willing to pay is not nearly enough to…
Use of my old Hotmail account has really snuck up on me as I end up caring more and more about all of the services with which it is associated. The last straw is Windows 8 login, but previous straws include Xbox, Zune, SkyDrive, and my Windows 7 Phone. I like the features and sync'ing associated with the Windows Live ID, but I don't like my old, spam filled, hotmail email address on the Live ID account.
A coworker told me about creating a Live ID from a custom domain, which sounded like just the ticket for me. Following the instructions above I was able to create a new deletethis.net Live ID but the next step of actually using this new Live ID was much more difficult. My first hope was there would be some way to link my new and old Live IDs so as to make them interchangeable. As it turns out there is a way to link Live IDs but all that does is make it easy to switch between accounts on Live Mail, SkyDrive and some other webpages.
Instead one must change over each service or start over depending on the service:
“From his first months in office, President Obamasecretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s main nuclear enrichment facilities, significantly expanding America’s first sustained use of cyberweapons, according to participants in the program.”
Very interesting - both technically as well as looking into the moral justifications the botnet operator provides. But equally interesting is the discussion on Hacker News: http://news.ycombinator.com/item?id=3960034. Especially the discussion on the Verified by Visa (3D Secure) system and how the goal is basically to move liability onto the consumer and off of the merchant or credit card company.

We never recovered the bicycle, of course. The lock itself wasn’t attacked at all, as you can see.

(via Feature: Google gets license to test drive autonomous cars on Nevada roads)
The coolest part of this article is that Nevada now has an autonomous vehicle license plate that’s red background and infinity on the left.
Breakdown of the STL’s implementation of next_permutation. Ever wondered how that works?
As Hammond explained what he did, the critic became agitated. Times are tough enough in journalism, he said, and now you’re going to replace writers with robots? “I just looked at him,” Hammond recalls, “and asked him: Have you ever seen a reporter at a Little League game? That’s the most important thing about us. Nobody has lost a single job because of us.” At least not yet.
This document defines several Structured Syntax Suffixes for use with media type registrations. In particular, it defines and registers the “+json”, “+ber”, “+der”, “+fastinfoset”, “+wbxml” and “+zip” Structured Syntax Suffixes, and updates the “+xml” Structured Syntax Suffix registration.
Javascript tool says if a photo is shopped. It can tell by looking at the pixels. Seriously. Links to cool presentation on the theory behind the algorithm behind the tool: http://www.wired.com/images_blogs/threatlevel/files/bh-usa-07-krawetz.pdf
Astronaut endorses destroying the moon!
The best exchange on the IAmA:
Ghostshirts it’s been a dream for a long time now, do you think that we’ll actually be able to blow up the moon in our lifetime?
RonGaran I truly believe that we can accomplish anything we set our minds on. We only need the will to do it
Seems generally bad to embed sensitive info in the URI (the http+aes URI scheme’s decryption key) similar to the now deprecated password field.
Use case is covered here: http://lists.w3.org/Archives/Public/ietf-http-wg/2012JanMar/0811.html. Also discussion including someone mentioning the issue above.
Fictional plot summaries of TNG S8 episodes. Like:
BE EXCITED.Promo on IFC for the upcoming Comedy Bang Bang TV show!!!
I am excited Paul.
One of the more limiting issues of writing client side script in the browser is the same origin limitations of XMLHttpRequest. The latest version of all browsers support a subset of CORS to allow servers to opt-in particular resources for cross-domain access. Since IE8 there's XDomainRequest and in all other browsers (including IE10) there's XHR L2's cross-origin request features. But the vast majority of resources out on the web do not opt-in using CORS headers and so client side only web apps like a podcast player or a feed reader aren't doable.
One hack-y way around this I've found is to use YQL as a CORS proxy. YQL applies the CORS header to all its responses and among its features it allows a caller to request an arbitrary XML, HTML, or JSON resource. So my network helper script first attempts to access a URI directly using XDomainRequest if that exists and XMLHttpRequest otherwise. If that fails it then tries to use XDR or XHR to access the URI via YQL. I wrap my URIs in the following manner, where type is either "html", "xml", or "json":
yqlRequest = function(uri, method, type, onComplete, onError) {
var yqlUri = "http://query.yahooapis.com/v1/public/yql?q=" +
encodeURIComponent("SELECT * FROM " + type + ' where url="' + encodeURIComponent(uri) + '"');
if (type == "html") {
yqlUri += encodeURIComponent(" and xpath='/*'");
}
else if (type == "json") {
yqlUri += "&callback=&format=json";
}
...