 Eric Lawrence
@ericlaw :
Eric Lawrence
@ericlaw :As the title suggests, spoilers for The Interview follow.
Towards the end of the movie, after Dave Skylark is shot, he miraculously has a bullet proof vest, blows up Kim Jong-un, finds a random tunnel and is picked up by Seal Team Six. These are the same details of the unbelievable scenario that Dave Skylark describes to Agent Lacey at the beginning of the movie.
This isn't a coincidence. Everything after Dave is shot is his fantasizing about how things should have gone as he dies in the interview chair. Unsurprisingly his fantasy closely matches his original ridiculous thoughts about how he would assassinate and escape.
This is similar to movies like Brazil in which the later fourth of the movie is the main character’s romantic fantasy as he is tortured and killed in real life. Or Total Recall where the end of the movie matches the description of the memories that the main character will have implanted at the beginning.
Its safe to assume that after Dave is killed, Aaron and Sook are captured and also killed.
Quadrilateral Cowboy gameplay video
“Quadrilateral Cowboy is a game we’ve been watching with great interest ever since Thirty Flights Of Loving creator Brendon Chung first debuted it last year. It’s about hacking, but not via irritating minigames or jargon-your-problems-away Hollywood magic. Instead, you learn basic (albeit fictional) code and take down everything from laser grids to gun emplacements with a twitch of your fingers and a wriggle of your brain. It’s already an extremely clever game, and it’s quite empowering despite the fact that you play as someone who probably couldn’t even heft an assault rifle - let alone fire one. Basically, it’s a wonderfully novel idea - more Neuromancer than Deus Ex - but words only do it so much justice. Thus, I’ve decided to play it for your enrichment, in hopes that you will understand why Quadrilateral should be driving your radar haywire.”
The story of Chris Knight, living in isolation in the woods of Maine for 27 years.
'Anyone who reveals what he's learned, Chris told me, is not by his definition a true hermit. Chris had come around on the idea of himself as a hermit, and eventually embraced it. When I mentioned Thoreau, who spent two years at Walden, Chris dismissed him with a single word: “dilettante.”'
'But still, I pressed on, there must have been some grand insight revealed to him in the wild…”Get enough sleep.”'
I don’t want to brag, but I’ve been telling that people all along and I didn’t have to live alone in the woods for decades.
A bogus SoundCloud takedown anecdote and a brief history of and issues with US copyright law.
Another reminder that the rest of the Western world has a public domain day every year in which new IP enters the public domain
On exploiting security issues in botnet C&C software:
Hackers “are learning that it’s not so easy to write secure code,” Toro says. “Most of us in the business of securing our applications and systems know that bulletproofing software is an extremely expensive and exhaustive undertaking. Malware creators who have to look to their own defences would have to slow down the production of new attacks.”
FYI, if you want to know what it looks like when you hack a hacker, look no further than the seminal 1995 film Hackers.
More than 90% of Americans believe that the US government is unduly influenced by money, and the Mayday.US super PAC is raising $5M to fund the election campaigns of politicians who’ll pledge to dismantle super PACs and enact other campaign finance reforms. They raised more than $1M in 30 days last month, and this month, the goal is $5M. It’s the brainchild of Lawrence Lessig, who’s going to run prototype the project by running five electoral campaigns in 2014, and use the lessons of those projects to win enough anti-corruption seats in 2016 to effect real change.
Again, I’m not able to contribute to Mayday.US, because I’m a Canadian and Briton. But I ask my American friends to put in $10, and promise that I’ll put CAD1000 into any comparable Canadian effort and/or £1000 into a comparable UK effort. We all win when countries embrace evidence-based policy guided by doing what’s best for its citizens, rather than lining the pockets of corrupting multinationals.
Please reblog!
gitfiti - abusing github commit history for the lulz
A script that abuses github submissions to draw pixel art in your github contributions pane.
I've put a new app on the Windows Store: Cloud Share. It connects the web to your Windows 8 share charm.
I did the development on GitHub and quite enjoyed myself. I wasn't sure I liked the game-ification of development in GitHub's dashboard showing you your longest development streak in days. However I realized that it encourages me to do work on my personal project and anything that aids in holding my attention on and helping me finish these projects is a good thing.
Some time back while I was working on getting the Javascript Windows Store app platform running on Windows Phone (now available on the last Windows Phone release!) I had an interesting bug that in retrospect is amusing.
I had just finished a work item to get accessibility working for JS WinPhone apps when I got a new bug: With some set of JS apps, accessibility appeared to be totally broken. At that time in development the only mechanism we had to test accessibility was a test tool that runs on the PC, connects to the phone, and dumps out the accessibility tree of whatever app is running on the phone. In this bug, the tool would spin for a while and then timeout with an error and no accessibility information.
My first thought was this was an issue in my new accessibility code. However, debugging with breakpoints on my code I could see none of my code was run nor the code that should call it. The code that called that code was a more generic messaging system that hit my breakpoints constantly.
Rather than trying to work backward from the failure point, I decided to try and narrow down the repro and work forwards from there. One thing all the apps with the bug had in common was their usage of WinJS, but not all WinJS apps demonstrated the issue. Using a binary search approach on one such app I removed unrelated app code until all that was left was the app's usage of the WinJS AppBar and the bug still occurred. I replaced the WinJS AppBar usage with direct usage of the underlying AppBar WinRT APIs and continued.
Only some calls to the AppBar WinRT object produced the issue:
var appBar = Windows.UI.WebUI.Core.WebUICommandBar.getForCurrentView();
// appBar.opacity = 1;
// appBar.closeDisplayMode = Windows.UI.WebUI.Core.WebUICommandBarClosedDisplayMode.default;
appBar.backgroundColor = Windows.UI.Colors.white; // Bug!
I eventually realized that predefined WinRT color values like Windows.UI.Colors.aqua would cause the issue while JS literal based colors didn't cause the issue (Windows.UI.Color is a WinRT struct which projects in JS as a JS literal object with the struct members as JS
object properties so its easy to write something like {r: 0, g: 0, b: 0, a: 0} to make a color) and I had been mixing both in my tests without realizing there would be a difference.
I debugged into the backgroundColor property setter that consumed the WinRT color struct to see what was different between Windows.UI.Colors.black and {a: 1, r: 0, g: 0, b: 0} and
found the two structs to be byte wise exactly the same.
On a hunch I tried my test app with only a reference to the color and otherwise no interaction with the AppBar and not doing anything with the actual reference to the color:
Windows.UI.Colors.black;. This too caused the issue. I knew that the implementation for these WinRT const values live in a DLL and guessed that something in the code to create these
predefined colors was causing the issue. I debugged in and no luck. Now I also have experienced crusty code that would do exciting things in its DllMain, the function that's called when a DLL is loaded into the process so I tried modifying my
C++ code to simply LoadLibrary the DLL containing the WinRT color definition, windows.ui.xaml.dll and found the bug still occurred! A short lived moment of relief as the world seemed to make
sense again.
Debugging into DllMain nothing interesting happened. There were interesting calls in there to be sure, but all of them behind conditions that were false. I was again stumped. On another hunch I tried renaming the DLL and only LoadLibrary'ing it and the bug went away. I took a different DLL renamed it windows.ui.xaml.dll and tried LoadLibrary'ing that and the bug came back. Just the name of the DLL was causing the issue.
I searched for the DLL name in our source code index and found hits in the accessibility tool. Grinning I opened the source to find that the accessibility tool's phone side service was trying to determine if a process belonged to a XAML app or not because XAML apps had a different accessibility contract. It did this by checking to see if windows.ui.xaml.dll was loaded in the target process.
At this point I got to fix my main issue and open several new bugs for the variety of problems I had just run into. This is a how to on writing software that is difficult to debug.
A reminder that those Doritos you love are trash:
Shortly after Disneyland opened in 1955, the founder of Frito-Lay got permission from Walt Disney to open a restaurant in Frontierland with a Mexican-ish theme. “Casa de Fritos” was, unsurprisingly, all about the Fritos. Customers got free Fritos, and Fritos were incorporated into many of the dishes. Fritos were dispensed by an animatronic vending machine that featured the terrifying “Frito Kid”asking his assistant “Klondike” to bring the bag up from a mineshaft. I guess the conceit is that Fritos were mined by Forty-Niners?
Casa de Fritos contracted their tortilla production to a company called Alex Foods. One of the salesmen from Alex Foods, making a delivery to Casa de Fritos, noticed stale tortillas in the garbage and gave the cook a little tip: fry them and sell them as chips instead of throwing them away. Casa de Fritos began making these fried, seasoned chips to enormous success, but didn’t report this new menu item to the Frito-Lay company.
Eventually Frito-Lay found out what they were doing with the chips, packaged them, and sold them by the truckload. See, dumpster diving works out sometimes!
Does it betray my innocence that I’m shocked by the amount of exec($_GET you can easily find on github? Hilarious comment thread on hacker news:
This is awful. Shell commands are not guaranteed to be idempotent, people! These should all be of the form exec($_POST, not exec($_GET.
Ringleader claimed to be an IT contractor, got access to bank computers.
Using social engineering to install a remote-controlled keyboard-video-mouse (KVM) switch on bank PCs, the gang managed to transfer millions to outside accounts in two separate jobs in April and July of 2013. They were caught attempting to rob a third bank in September.

Internet Archive lets you play one of the earliest computer games Space War! emulated in JavaScript in the browser.
This entry covers the historical context of Space War!, and instructions for working with our in-browser emulator. The system doesn’t require installed plugins (although a more powerful machine and recent browser version is suggested).
The JSMESS emulator (a conversion of the larger MESS project) also contains a real-time portrayal of the lights and switches of a Digital PDP-1, as well as links to documentation and manuals for this $800,000 (2014 dollars) minicomputer.
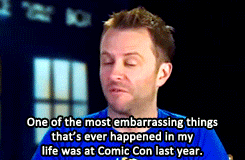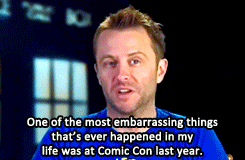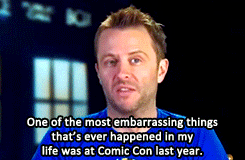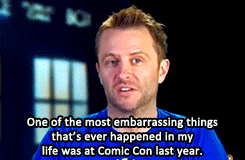









Matt & David on Chris Hardwick’s Comic Con Blunder (x)
requested by tennanttardistime
Bonus Chris Hardwick in costume:

Just a quick tutorial on exploiting heartbleed for session hijacking. Is it worse to use https than http today?
Adds the yield keyword enabling you to write JS code that sort of looks like C# await.
Overview
First-class coroutines, represented as objects encapsulating suspended execution contexts (i.e., function activations). Prior art: Python, Icon, Lua, Scheme, Smalltalk.

Victorian Trolling: How Con Artists Spammed in a Time Before Email
The main difference between 21st-century scams and those of centuries past is one of delivery method.Read more. [Image: Wikimedia Commons/Benjamin Breen]
 [Testing Cat-Human Translator] Scientist: Cat, what is your name? Cat: I AM KANG THE
DESTROYER Owner: It's not working. His name is Socks.
[Testing Cat-Human Translator] Scientist: Cat, what is your name? Cat: I AM KANG THE
DESTROYER Owner: It's not working. His name is Socks.