def nextServerCallback(self, data):
parsed_data = json.loads(data)
# Chunk was wrong!
if not parsed_data['success']:
# Defend against timing attacks
remaining_time = self.expectedRemainingTime()
self.log_info('Going to wait %s seconds before responding' %
remaining_time)
reactor.callLater(remaining_time, self.sendResult, False)
return
self.checkNext()A Slower Speed of Light Official Trailer — MIT Game Lab (by Steven Schirra)
“A Slower Speed of Light is a first-person game in which players navigate a 3D space while picking up orbs that reduce the speed of light in increments. A custom-built, open-source relativistic
graphics engine allows the speed of light in the game to approach the player’s own maximum walking speed. Visual effects of special relativity gradually become apparent to the player, increasing
the challenge of gameplay. These effects, rendered in realtime to vertex accuracy, include the Doppler effect; the searchlight effect; time dilation; Lorentz transformation; and the runtime
effect.
A production of the MIT Game Lab.
Play now for Mac and PC! http://gamelab.mit.edu/games/a-slower-speed-of-light/”

“Jon Hamm And Adam Scott’s ‘greatest Event In Tv
History’ Was A Tribute To A Forgotten ’80s Classic
If you know more about Simon and Simon than its intro and general premise, you’re better at TV than I am. If you’ve never heard of Simon and Simon, you’re the BEST at TV because, honestly, Simon
& Simon — a CBS series about two mismatched brothers who ran a private detective service; it ran for eight seasons — wasn’t good.
Source: Uproxx”

How the 8.5” x 11” Piece of Paper Got Its Size
Why do we use a paper size that is so unfriendly for the basic task of reading? According to a very interesting post by Paul Stanley, the rough dimensions of office paper evolved to accommodate handwriting and typewriters with monospaced fonts, both of which rendered many fewer characters per line. “Typewriters,” he explains, “produced 10 or 12 characters per inch: so on (say) 8.5 inch wide paper, with 1 inch margins, you had 6.5 inches of type, giving … around 65 to 78 characters.” This, he says, is “pretty close to ideal.”
Read more. [Image: Picsfive/Shutterstock]
Level 4 and level 6 of the Stripe CTF had solutions around XSS.
> Registered Users
<%= user[:username] %>
(password: <%= user[:password] %>, last active <%= last_active %>)
The level 4 web application lets you transfer karma to another user and in doing so you are also forced to expose your password to that user. The main user page displays a list of users who have transfered karma to you along with their password. The password is not HTML encoded so we can inject HTML into that user's browser. For instance, we could create an account with the following HTML as the password which will result in XSS with that HTML:
Code review red flags in this case included lack of encoding when using user controlled content to create HTML content, storing passwords in plain text in the database, and displaying passwords generally. By design the web app shows users passwords which is a very bad idea.
...
def self.safe_insert(table, key_values)
key_values.each do |key, value|
# Just in case people try to exfiltrate
# level07-password-holder's password
if value.kind_of?(String) &&
(value.include?('"') || value.include?("'"))
raise "Value has unsafe characters"
end
end
conn[table].insert(key_values)
endThis web app does a much better job than the level 4 app with HTML injection. They use encoding whenever creating HTML using user controlled data, however they don't use encoding when injecting JSON data into script (see post_data initialization above). This JSON data is the last five most recent messages sent on the app so we get to inject script directly. However, the system also ensures that no strings we write contains single or double quotes so we can't get out of the string in the JSON data directly. As it turns out, HTML lets you jump out of a script block using no matter where you are in script. For instance, in the middle of a value in some JSON data we can jump out of script. But we still want to run script, so we can jump right back in. So the frame so far for the message we're going to post is the following:
|
From: David Risney
Views: 75
    
0 ratings
|
||
| Time: 00:43 | More in People & Blogs |
|
From: David Risney
Views: 69
    
0 ratings
|
||
| Time: 00:53 | More in People & Blogs |

(via Pareidoloop)
“Phil McCarthy’s Pareidoloop overlays randomly generated polygons on top of one another until facial recognition software recognizes a human face. Can’t sleep, at SIGGRAPH! [via @Brandonn]”
(via Classic pro-science-careers music video PSA: Chemical Party)
Xeni says: “The EU wasn’t always so terrible at promoting science careers through funny internet music videos! (thanks, Guido)”
Waxy roundup of DMCA takedown process stupidity.
“So the Scripps TV broadcasts are indexed by YouTube, and the Content ID robots do the rest. And because Content ID disputes are judged by the copyright holder, complaints are routinely ignored or denied.”
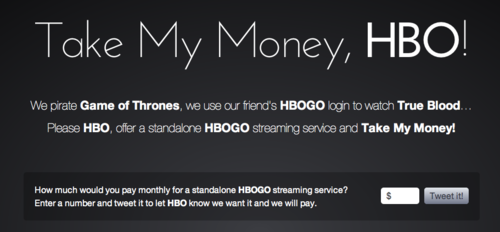
The conversation surrounding how to liberate HBO from its cable partners and create the entertainment utopia viewers have long desired has been fascinating.
The resulting analyses of the numbers has pretty much shown that the amount people are willing to pay is not nearly enough to…
I'm done playing Fez. The style is atmospheric retro nastalgia and on the surface the gameplay is standard 2D platformer with one interesting Flatland style game mechanic but dig deeper to find Myst style puzzles. Despite the following I thoroughly enjoyed the game and would recommend it to anyone intrigued by the previous. Five eighths through the game I ran into one of the game's infamous Fez save game breaking issues, but I enjoyed the game enough that I started over before any patches were released and had no further issues.
While playing the game I created some tools to help keep track of my Fez notes (spoilers) including a Pixelated Image Creator that makes it easy to generate data URIs for large, black and white pixelated images, and (spoilers) a Fez Transliteration Tool to help me translate the in-game writing system.
Dark Patterns are UI patterns used to trick users into doing things they’d otherwise rather not: buy traveler’s insurance, click on ads, etc. Covers the anti-patterns and how we as technical folk can help stop this.
BE EXCITED.Promo on IFC for the upcoming Comedy Bang Bang TV show!!!
I am excited Paul.
What Target discovered fairly quickly is that it creeped people out that the company knew about their pregnancies in advance.
“If we send someone a catalog and say, ‘Congratulations on your first child!’ and they’ve never told us they’re pregnant, that’s going to make some people uncomfortable,” Pole told me. “We are very conservative about compliance with all privacy laws. But even if you’re following the law, you can do things where people get queasy.”
As a professional URI aficionado I deal with various levels of ignorance on URI percent-encoding (aka URI encoding, or URL escaping).
Worse than the lame blog comments hating on percent-encoding is the shipping code which can do actual damage. In one very large project I won't name, I've fixed code that decodes all percent-encoded octets in a URI in order to get rid of pesky percents before calling ShellExecute. An unnamed developer with similar intent but clearly much craftier did the same thing in a loop until the string's length stopped changing. As it turns out percent-encoding serves a purpose and can't just be removed arbitrarily.
Percent-encoding exists so that one can represent data in a URI that would otherwise not be allowed or would be interpretted as a delimiter instead of data. For example, the space character (U+0020) is not allowed in a URI and so must be percent-encoded in order to appear in a URI:
http://example.com/the%20path/
http://example.com/the path/
For an additional example, the question mark delimits the path from the query. If one wanted the question mark to appear as part of the path rather than delimit the path from the query, it must be percent-encoded:
http://example.com/foo%3Fbar
http://example.com/foo?bar
/foo" from the query "bar". And in the first, the querstion mark is percent-encoded and so
the path is "/foo%3Fbar".
There’s weird stuff you’d think is public domain but isn’t including Martin Luther King Jr.‘s “I Have a Dream” speech. FTA: ”If you want to watch the whole thing, legally, you’ll need to get the $20 DVD.
That’s because the King estate, and, as of 2009, the British music publishing conglomerate EMI Publishing, owns the copyright of the speech and its recorded performance.”