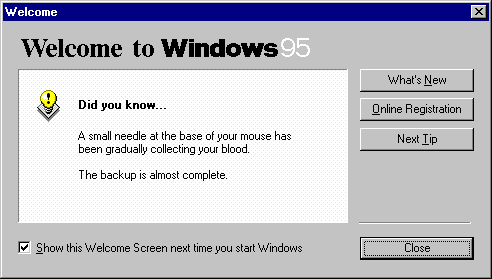
Some very H. P. Lovecraft style redesigns of some classic Win95 UI.


Hey, guys, remember this?
Please don’t forget to go out and vote! Find you polling place here.
Voting complete. Now we get more Arrested Development.
According to the links within this article, although the root URI of the router requires authentication, the /password.cgi URI doesn’t and the resulting returned HTML contains (but does not display) the plaintext of the password, as well as an HTML FORM to modify the password that is exploitable by CSRF.
The attack… infected more than 4.5 million DSL modems… The CSRF (cross-site request forgery) vulnerability allowed attackers to use a simple script to steal passwords required to remotely log in to and control the devices. The attackers then configured the modems to use malicious domain name system servers that caused users trying to visit popular websites to instead connect to booby-trapped imposter sites.
Eric gets the most entertaining mail.
You have failed to comply with them after all the warning and instructions given to you, but since you are also among the terrorist we are facing in the country, I will personal make sure that I wipe away the crime in the state and I promise you that you will definitely pay with your life because I am here to protect the interest of my people and not to put them in shame, you suppose to support this government and not to spoil it.
Megabox is an ad-replacer - replacing ads on the web as you browse with its own. Ignoring security concerns, I hope this doesn’t result in over prescriptive laws that endanger things like Greasemonkey.
To listen to songs through Megabox, users will have two options—purchasing the music through the service, or installing “Megakey” software onto their computer to listen for free. The Megakey software, as Dotcom explained to Torrentfreak, acts like ad-blocking software—except that it isn’t. Megakey allows most advertisements to appear, but replaces about 15 percent of the ads served up by websites with ads hosted by Megabox.
Welcome news. Glad to hear they’re looking for improvements.
… the USPTO has also worked with Stack Exchange, … to create a new site called Ask Patents. … Examiners or others looking for prior art can post questions about a specific application, and members of the general public can respond with evidence that an applicant was not the first to invent the subject matter of the application.

How the 8.5” x 11” Piece of Paper Got Its Size
Why do we use a paper size that is so unfriendly for the basic task of reading? According to a very interesting post by Paul Stanley, the rough dimensions of office paper evolved to accommodate handwriting and typewriters with monospaced fonts, both of which rendered many fewer characters per line. “Typewriters,” he explains, “produced 10 or 12 characters per inch: so on (say) 8.5 inch wide paper, with 1 inch margins, you had 6.5 inches of type, giving … around 65 to 78 characters.” This, he says, is “pretty close to ideal.”
Read more. [Image: Picsfive/Shutterstock]
An analysis of leaked PIN numbers.
… nearly 11% of the 3.4 million passwords are 1234 !!!
A howto on making your video game accessible to those with disabilities (blind, color blind, deaf, etc)
The AbleGamers Foundation has created a 48-page document it hopes will serve as a how-to guide for game developers and publishers on how to create more accessible games. The in-depth guide by the disability non-profit covers in great detail how to make games available to those with varying degrees of mobility, hearing, visual and cognitive issues.
Level 4 and level 6 of the Stripe CTF had solutions around XSS.
> Registered Users
<%= user[:username] %>
(password: <%= user[:password] %>, last active <%= last_active %>)
The level 4 web application lets you transfer karma to another user and in doing so you are also forced to expose your password to that user. The main user page displays a list of users who have transfered karma to you along with their password. The password is not HTML encoded so we can inject HTML into that user's browser. For instance, we could create an account with the following HTML as the password which will result in XSS with that HTML:
Code review red flags in this case included lack of encoding when using user controlled content to create HTML content, storing passwords in plain text in the database, and displaying passwords generally. By design the web app shows users passwords which is a very bad idea.
...
def self.safe_insert(table, key_values)
key_values.each do |key, value|
# Just in case people try to exfiltrate
# level07-password-holder's password
if value.kind_of?(String) &&
(value.include?('"') || value.include?("'"))
raise "Value has unsafe characters"
end
end
conn[table].insert(key_values)
endThis web app does a much better job than the level 4 app with HTML injection. They use encoding whenever creating HTML using user controlled data, however they don't use encoding when injecting JSON data into script (see post_data initialization above). This JSON data is the last five most recent messages sent on the app so we get to inject script directly. However, the system also ensures that no strings we write contains single or double quotes so we can't get out of the string in the JSON data directly. As it turns out, HTML lets you jump out of a script block using no matter where you are in script. For instance, in the middle of a value in some JSON data we can jump out of script. But we still want to run script, so we can jump right back in. So the frame so far for the message we're going to post is the following:

When they went to the Moon, they received the same per diem compensation as they would have for being away from base in Bakersfield: eight dollars a day, before various deductions (like for accommodation, because the government was providing the bed in the spaceship).
Apollo 11’s Astronauts Received an $8 Per Diem for the Mission to the Moon
The astronauts of Apollo 11: Intrepid explorers. Inspirational heroes. Government employees.
Read more. [Image: Reuters]
dnsxss tool helps you inject via DNS
…what it does is, essentially, respond to DNS requests for CNAME, MX, TXT, and NS records with Javascript code. … how about SQL injection?