The story of Chris Knight, living in isolation in the woods of Maine for 27 years.
'Anyone who reveals what he's learned, Chris told me, is not by his definition a true hermit. Chris had come around on the idea of himself as a hermit, and eventually embraced it. When I mentioned Thoreau, who spent two years at Walden, Chris dismissed him with a single word: “dilettante.”'
'But still, I pressed on, there must have been some grand insight revealed to him in the wild…”Get enough sleep.”'
I don’t want to brag, but I’ve been telling that people all along and I didn’t have to live alone in the woods for decades.
A DEFCON talk “The Secret Life of SIM Cards” that covers running apps on your SIM card. Surprisingly they run a subset of Java and execute semi-independent of the Phone’s OS.
 Mathematically speaking, any two ducks are already in a row. In order to get your
ducks in a row, own exactly two ducks.
Mathematically speaking, any two ducks are already in a row. In order to get your
ducks in a row, own exactly two ducks.
Level3 counters Verizon’s recent post about Netflix traffic.
"In fact, Level 3 has asked Verizon for a long time to add interconnection capacity and to deliver the traffic its customers are requesting from our customers, but Verizon refuses."
An interesting way to use the report-uri feature of CSP to detect if a user is logged into Google, Facebook etc.
Applied game theory 101: Valve’s Steam Summer Sale involves a meta game with teams of Steam users competing for daily prizes. On Reddit the players join together to take turns winning daily. Valve gets wise and performs an existential attack, changing the rules to make it harder for players to want to coordinate.
Still, that all the players joined together to game the system gives me hope for humanity. Its a self organized solution to a tragedy of the commons problem. Only in this case the tragedy is by design and is updated to be more tragic.
A bogus SoundCloud takedown anecdote and a brief history of and issues with US copyright law.
Another reminder that the rest of the Western world has a public domain day every year in which new IP enters the public domain
From Inside Edward Snowden’s Life as a Robot:
Wizner had to jump on a phone call during a meeting with his whistleblower client. When he got off the phone, he found that Snowden had rolled the bot into civil liberties lawyer Jameel Jaffer’s office and was discussing the 702 provision of the Foreign Intelligence Surveillance Act. “It was kind of cool,” Wizner says.
It is neat but they’re marketing video is at times strangely terrifying. Put different music on when the Susan-bot comes up behind the unknowing Mark and this could be a horror movie trailer.
On exploiting security issues in botnet C&C software:
Hackers “are learning that it’s not so easy to write secure code,” Toro says. “Most of us in the business of securing our applications and systems know that bulletproofing software is an extremely expensive and exhaustive undertaking. Malware creators who have to look to their own defences would have to slow down the production of new attacks.”
FYI, if you want to know what it looks like when you hack a hacker, look no further than the seminal 1995 film Hackers.
Mario Maker - Design Mario levels on the Wii U. Time to break out my Mario level design documents from when I was 8.

Netflix responds to Verizon’s cease & desist letter. Somehow I doubt that Verizon will bite on your offer to work together to increase network transparency Netflix. Nice suggestion though.
More than 90% of Americans believe that the US government is unduly influenced by money, and the Mayday.US super PAC is raising $5M to fund the election campaigns of politicians who’ll pledge to dismantle super PACs and enact other campaign finance reforms. They raised more than $1M in 30 days last month, and this month, the goal is $5M. It’s the brainchild of Lawrence Lessig, who’s going to run prototype the project by running five electoral campaigns in 2014, and use the lessons of those projects to win enough anti-corruption seats in 2016 to effect real change.
Again, I’m not able to contribute to Mayday.US, because I’m a Canadian and Briton. But I ask my American friends to put in $10, and promise that I’ll put CAD1000 into any comparable Canadian effort and/or £1000 into a comparable UK effort. We all win when countries embrace evidence-based policy guided by doing what’s best for its citizens, rather than lining the pockets of corrupting multinationals.
Please reblog!
"A routine request in Florida for records detailing the use of a surveillance tool known as stingray turned extraordinary Tuesday when the U.S. Marshals Service seized the documents before local police could release them."
Also what about the part where the PD reveals that its been using the stingray a bunch without telling any court and blames that on the manufacturer’s NDA.
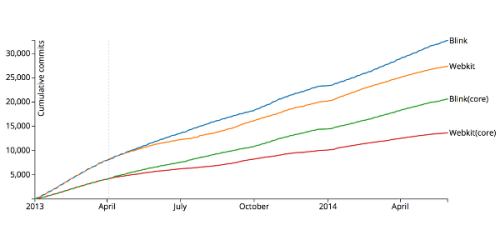
A high-profile fork: one year of Blink and Webkit
Some stats and analysis at a very high level of the Blink fork from Webkit.
Morgan Freeman’s unboxing videos. This episode: unboxing Gwyneth Paltrow’s head.

Nieman Journalism Lab - Who’s behind that tweet? Here’s how 7 news orgs manage their Twitter and Facebook accounts
Google’s XSS training game. Learn how to find XSS issues for fun and profit.

Kickstarter - Bring Reading Rainbow Back for Every Child, Everywhere.
The best hack I’ve seen in a while. With no way to disable the shutter sound from the capture photo API, the developer creates the inverse waveform of the shutter sound and plays it at the same time to cancel out the shutter sound.