
The Verge has the best earliest coverage of the Microsoft Surface press conference and pretty photos.
Microsoft Surface event 2012: everything you need to know
This page is a high-level overview of the project and provides guidence on how to implement the intents in your applications without the need for the you to understand the entire spec.
| HTTP Content Coding Token | gzip | deflate | compress |
|---|---|---|---|
| An encoding format produced by the file compression program "gzip" (GNU zip) | The "zlib" format as described in RFC 1950. | The encoding format produced by the common UNIX file compression program "compress". | |
| Data Format | GZIP file format | ZLIB Compressed Data Format | The compress program's file format |
| Compression Method | Deflate compression method | LZW | |
| Deflate consists of LZ77 and Huffman coding | |||
Compress doesn't seem to be supported by popular current browsers, possibly due to its past with patents.
Deflate isn't done correctly all the time. Some servers would send the deflate data format instead of the zlib data format and at least some versions of Internet Explorer expect deflate data format instead of zlib data format.
451 Unavailable for Legal Reasons: The 451 status code is optional; clients cannot rely upon its use. It is imaginable that certain legal authorities may wish to avoid transparency, and not only forbid access to certain resources, but also disclosure that the restriction exists.
That was fast.
Summary of one of the Chrome security exploits from pwn2own. Basically XSS into the chrome URI scheme which gives access to special APIs.
So this is another Stuxnet by Israel/US?
The analysis reinforces theories that researchers from Kaspersky Lab, CrySyS Lab, and Symantec published almost two weeks ago. Namely, Flame could only have been developed with the backing of a wealthy nation-state. … “It’s not a garden-variety collision attack, or just an implementation of previous MD5 collisions papers—which would be difficult enough,” Matthew Green, a professor specializing in cryptography in the computer science department at Johns Hopkins University, told Ars. “There were mathematicians doing new science to make Flame work.”

[via motherjones]:
Sticking to an exercise routine takes dedication, and many fitness junkies swear that a running companion can be a huge help. That’s why researchers have developed “Joggobot,” a quad-rotor helicopter drone designed to motivate joggers by flying in front of them.
The aerial robot uses its camera to spot a colorful pattern on a T-shirt worn by the jogger, and flies at a safe distance ahead. The runner can control Joggobot using a smartphone: In “companion mode,” the drone simply maintains the jogger’s pace; in “coach mode,” it pushes its human trainee a little faster.
Don’t worry, there’s a video
Science!
Maybe it should chase you instead?
Waxy roundup of DMCA takedown process stupidity.
“So the Scripps TV broadcasts are indexed by YouTube, and the Content ID robots do the rest. And because Content ID disputes are judged by the copyright holder, complaints are routinely ignored or denied.”
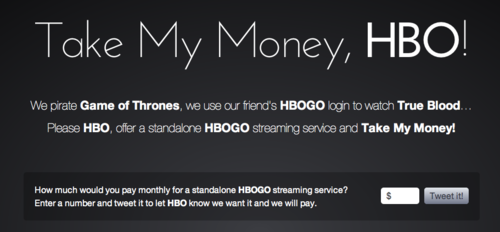
The conversation surrounding how to liberate HBO from its cable partners and create the entertainment utopia viewers have long desired has been fascinating.
The resulting analyses of the numbers has pretty much shown that the amount people are willing to pay is not nearly enough to…
Neat demo of Visvalingam’s line simplification algorithm in JavaScript applied to a map of the US.
To simplify geometry to suit the displayed resolution, various line simplification algorithms exist. While Douglas–Peucker is the most well-known, Visvalingam’s algorithm may be more effective and has a remarkably intuitive explanation: it progressively removes points with the least-perceptible change.
Jet Set Radio HD coming soon with awesome soundtrack promised. Exciting!
Flickr parses the exif out of images using Web Workers, and Blob (File API)!
“From his first months in office, President Obamasecretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s main nuclear enrichment facilities, significantly expanding America’s first sustained use of cyberweapons, according to participants in the program.”
A great JS API to add Clippy or other agents to your website! Make them talk, dance, gesture, etc
Star Trek’s hypospray apparently already existed and has been patented since 1960.
The second episode of Comedy Bang! Bang! available for your viewing pleasure immediately. (episode one not yet available)
Very interesting - both technically as well as looking into the moral justifications the botnet operator provides. But equally interesting is the discussion on Hacker News: http://news.ycombinator.com/item?id=3960034. Especially the discussion on the Verified by Visa (3D Secure) system and how the goal is basically to move liability onto the consumer and off of the merchant or credit card company.
Fixed in Windows 8 is intra-line tab completion - you can try it out on the Windows 8 Consumer Preview now. If you open a command prompt, type a command, then move your cursor back into a token in the middle of the command and tab complete, the tab completion works on that whitespace delimited token and doesn't erase all text following the cursor. Like it does in pre Windows 8. And annoys the hell out of me. Yay!
Its all quite shocking.
Fourth , when I explained that the blog publisher had received music from the industry itself, a government attorney replied that authorization was an “affirmative defense” that need not be taken into account by the government in carrying out the seizure. That was stunning.