2009 May 13, 10:17"Harvard's Office for Scholarly Communication has brought Kenneth Crews of Columbia Law School to talk about "Protecting Your Scholarship: Copyrights, Publication Agreements, and Open Access.""
 harvard kenneth-crews berkman david-weinberger blog copyright talk live-blog
harvard kenneth-crews berkman david-weinberger blog copyright talk live-blog 2009 May 12, 2:32If Hulu removes programming or Netflix doesn't make something available to watch instantly, its a safe bet it wasn't their idea to make their service worse. '"Whose retarded idea was that?" Well, not
Hulu's. The move was taken at the network's request. Powerful forces are working against free, legal online TV - and the decision to pull Sunny may have made that show the canary in the server farm.'
 hulu business wired tv web internet
hulu business wired tv web internet 2009 May 8, 8:23
I watched the new Star Trek movie Thursday morning, along with many others who work on Windows. Microsoft rented out a theater and played the movie on all screens. I greatly enjoyed the movie!
Spoilers follow... I'm obviously not the biggest Star Trek nerd (or at least TOS nerd) since I didn't even pick up on the fact that Kirk's dad being dead was a discrepancy from the TV series. I
only figured out the alternate time-line stuff when they killed most of the Vulcans. I was just surprised they didn't set right what once went wrong by the end of the movie with some more time
travel magic to bring back Vulcan. On that note, I'm pretty sure the Spock-Spock conversation at the end, is Nimoy Spock sending Sylar Spock off to school so that Nimoy Spock can get freaky
repopulating the Vulcan race. Although at first after his 'two places at once' comment I thought he was saying... something else. Also, was the main evil guy a random miner turned psycho? And his
crazy looking spaceship that destroys the Federation fleet was just a mining vessel from the future? Once they invent time travel anybody can get drunk, go back in time, and conquer Earth.
 personal2 nerd movie star-trek spoliers time-travel
personal2 nerd movie star-trek spoliers time-travel 2009 May 3, 10:03"Architectural Styles and the Design of Network-based Software Architectures - DISSERTATION submitted in partial satisfaction of the requirements for the degree of DOCTOR OF PHILOSOPHY in Information
and Computer Science by Roy Thomas Fielding 2000"
 http rest paper web architecture development api webservices roy-fielding
http rest paper web architecture development api webservices roy-fielding 2009 May 3, 10:36
Looking at the HTTP traffic of Netflix under Fiddler I could see the HTTP request that added a movie to my queue and didn't see anything obvious that would
prevent a CSRF. Sure enough its pretty easy to create a page that, if the user has set Netflix to auto-login, will add movies to the user's queue without their knowledge. I thought this was pretty
neat, because I could finally get people to watch Primer. However, when I searched for Netflix CSRF I found that this issue has been known and reported to Netflix since 2006. Again my thoughts stolen from me and the
theif doesn't even have the common decency to let me have the thought first!
With this issue known for nearly three years its hard to continue calling it an issue. Really they should just document it in their API docs and be
done with it. Who knows what Netflix based web sites and services they'll break if they try to change this behavior? For instance, follow this link to add my Netflix recommended movies to your queue.
 technical stolen-thoughts csrf netflix security
technical stolen-thoughts csrf netflix security 2009 Apr 29, 1:06More than three decades after the Clean Water Act, iconic American waterways like the Chesapeake Bay and Puget Sound are in perilous condition and facing new sources of contamination.
 todo via:jen video pbs environment
todo via:jen video pbs environment 2009 Apr 23, 5:22"Network Monitor 3.3 is a protocol analyzer. It allows you to capture network traffic, view and analyze it. Version 3.3 is an update and replaces Network Monitor 3.2. Network Monitor 3.x is a
complete overhaul of the previous Network Monitor 2.x version."
 microsoft network traffic netmon free msdn windows
microsoft network traffic netmon free msdn windows 2009 Apr 15, 7:42"If you're like us, you live in constant fear of slipping into a wormhole and getting spit out in the 13th century, and the only real useful knowledge you have for your ignorant ancestors is 'watch
out for that Hitler guy' and 'some of the Popes are evil.'" Its like they're inside my head! Love this shirt and poster telling you everything you need to know in case you accidentally fall back in
time.
 time-travel time shirt poster wishlist gift awesome
time-travel time shirt poster wishlist gift awesome 2009 Apr 14, 9:26
 I've made a QR Encode accelerator around Google Chart's QR code generator. QR codes are 2D bar-codes that can store (among other things) URLs and have good support on mobile
phones. The accelerator I've written lets you generate a QR code for a selected link and view it in the preview window. In combination with the ZXing
bar-code scanner app for my Android cellphone, its easy for me to right click on a link in IE8 on my desktop PC, hover over the QR Encode accelerator to have the link's associated QR code
displayed, and then with my phone read that QR code to open my phone's browser to the URL contained inside. Its much easier to browse around in the comfort of my desktop and only send particular
URLs to my cellphone as necessary.
I've made a QR Encode accelerator around Google Chart's QR code generator. QR codes are 2D bar-codes that can store (among other things) URLs and have good support on mobile
phones. The accelerator I've written lets you generate a QR code for a selected link and view it in the preview window. In combination with the ZXing
bar-code scanner app for my Android cellphone, its easy for me to right click on a link in IE8 on my desktop PC, hover over the QR Encode accelerator to have the link's associated QR code
displayed, and then with my phone read that QR code to open my phone's browser to the URL contained inside. Its much easier to browse around in the comfort of my desktop and only send particular
URLs to my cellphone as necessary.
 technical boring accelerator android barcode ie8 google qr code
technical boring accelerator android barcode ie8 google qr code 2009 Apr 12, 6:36"MonasticXML.org is a look at XML from a different angle, focusing on what markup is best at rather than what markup can do to solve a particular problem or set of problems. While XML is powerful,
developers seem insistent on using XML in ways which seem convenient for a moment but which cause much greater trouble down the line to both their projects and to markup itself."
 xml howto tips
xml howto tips 2009 Apr 10, 9:48
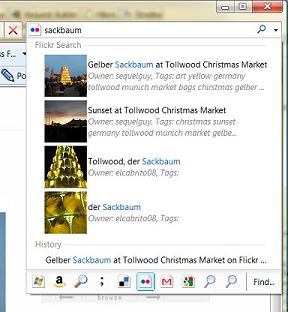 A while ago I promised to say how an xsltproc Meddler script would be useful and the general answer is
its useful for hooking up a client application that wants data from the web in a particular XML format and the data is available on the web but in another XML format. The specific case for this
post is a Flickr Search service that includes IE8 Visual Search Suggestions. IE8
wants the Visual Search Suggestions XML format and Flickr gives out search data in their Flickr web API XML format.
A while ago I promised to say how an xsltproc Meddler script would be useful and the general answer is
its useful for hooking up a client application that wants data from the web in a particular XML format and the data is available on the web but in another XML format. The specific case for this
post is a Flickr Search service that includes IE8 Visual Search Suggestions. IE8
wants the Visual Search Suggestions XML format and Flickr gives out search data in their Flickr web API XML format.
So I wrote an XSLT to convert from Flickr Search XML to Visual Suggestions XML and used my xsltproc Meddler script to actually
apply this xslt.
After getting this all working I've placed the result in two places: (1) I've updated the xsltproc Meddler script to include this XSLT and an
XML file to install it as a search provider - although you'll need to edit the XML to include your own Flickr API key. (2) I've created a service for this so you can just install the Flickr search provider if you're interested in having the functionality and don't care about the implementation. Additionally, to the
search provider I've added accelerator preview support to show the Flickr slideshow which I think looks snazzy.
Doing a quick search for this it looks like there's at least one other such implementation, but mine has the distinction of being done through XSLT which I provide, updated XML namespaces to work
with the released version of IE8, and I made it so you know its good.
 meddler xml ie8 xslt flickr technical boring search suggestions
meddler xml ie8 xslt flickr technical boring search suggestions 2009 Apr 9, 8:56Someone implemented the Ironic Sans artificial sundial clock concept! "Last year David Friedman published on his blog Ironic Sans an interesting design concept for something that he called The
Bulbdial Clock. That's like a sundial, but with better resolution-- not just an hour hand, but a minute and second hand as well, each given as a shadow from moving artificial light sources (bulbs).
We've recently put together a working bulbdial clock, with an implementation somewhat different from that of the original concept."
 howto diy clock led sundial via:swannman
howto diy clock led sundial via:swannman 2009 Apr 7, 12:14This makes plenty of sense, that a site should be able to check if a protocol handler exists for some URI scheme, but it'd be nice if this were some sort of declaritive fallback plan rather than
having to do it all with script. "The HTML5 standard function registerProtocolHandler() should probably remain void as in standard, but WhatWG could invent yet another boolean
protocolRegistered("area"), with the only argument (protocol name as string), to check whether a protocol is registered."
 html5 registerProtocolHandler html script url uri scheme protocol
html5 registerProtocolHandler html script url uri scheme protocol 2009 Apr 7, 9:02
I'm a big fan of the concept of registerProtocolHandler in HTML 5 and in FireFox 3, but not quite the implementation. From a high level, it allows web apps to register themselves as
handlers of an URL scheme so for (the canonical) example, GMail can register for the mailto URL scheme. I like the concept:
- Better integration of web apps with your system.
- Its easy for web apps to do.
- Links to URNs can now take the user to the sites the user prefers for the sort of thing identified by the URN. For example, if I have a physical address in HTML, instead of making that an http
link to Yahoo Maps, I can make the link a geo scheme URI and those who follow the link will get their preferred mapping site that
has registered for that scheme. Actually, looking at the geo scheme's RFC, maybe I'd rather use some other URN scheme to represent the physical location, but you get the point.
However, the way its currently spec'ed out I don't like the following:
- There's no way to know if you are the handler for a particular URL scheme which is an important question for web app URL protocol handler authors.
- There's no way to fallback to an http URL in the case that a particular URL scheme isn't registered. A suggested solution to testing the registration of a scheme is for browsers to provide an additional script method
to check if a scheme is registered. I don't like the idea of writing script that walks over all my page's links and rewrites them based on that method. I'd much rather see a declarative and
backwards compatible fallback mechanism, although I don't know what that would look like.
- There's no way to register for a namespace within the urn scheme URI, the info scheme URI, or the tag scheme URI. I want to register
info:lccn/... (Library of Congress Card Number identifiers) to LibraryThing or Amazon and I want to register urn:duri:... (dated URIs) to the Web Archive, among other things.
- Will this result in a proliferation of unregistered URL schemes with clashing namespaces? The ESW Wiki notes why this would be bad.
- And last, although this is nitpickier than the rest, I don't like the '%s' syntax used in the registration method. I'd much rather pass in an URL template, like the URL template used
in OpenSearch. If an URL template is used for matching rather than registering against a particular URL scheme, this could also allow for registering a namespace within a URN. For example
something along the lines of:
registerProtocolHandler("info:lccn/{lccnID}", "htttp://www.librarything.com/search_works.php?q={lccnID}", "LibraryThing LCCN")
 url template registerprotocolhandler firefox technical url scheme protocol boring html5 uri urn
url template registerprotocolhandler firefox technical url scheme protocol boring html5 uri urn 2009 Apr 1, 12:32Spped Rabbit Pizza's "IE8 Explorer" pizza: 8 slices, 8 ingredients, 8 Euros.
 humor pizza ie8 ie france
humor pizza ie8 ie france 2009 Apr 1, 9:32'To help stem the downward spiral of the United States economy Congress has proposed a new dollar symbol. "Updating fonts on the world's computers and devices would be a huge economic stimulus" said
one representative after a late night session of the newly formed House Subcommittee - Font Economic Stimulus Technology Relief (FESTR). "The dollar is a shadow of its former self and the new design
reflects this."'
 art design humor font dollar-sign typography government economics
art design humor font dollar-sign typography government economics 2009 Apr 1, 9:20"Consolidating its position at the cutting edge of new media technology, the Guardian today announces that it will become the first newspaper in the world to be published exclusively via Twitter"
 humor news twitter journalism newspaper
humor news twitter journalism newspaper 2009 Mar 26, 2:24"Yesterday's remix challenge -- to mock the ridiculous new "anti-terrorism" posters the London police have put up that tell you to spy on your neighbors -- was a smashing success. I've collected the
25 or so that came in to date below". I enjoyed: "A bomb won't go off here because people tend to be quite nice really." "Terribly convenient, isn't it? Incriminating evidence left right out where
you'll spot it and call it in..." "A bomb won't go off here because the true likelihood of you being the victim of a terror attack is really very low, especially when compared to other causes of
death or injury."
 humor politics poster paranoia security via:boingboing.comments photoshop privacy
humor politics poster paranoia security via:boingboing.comments photoshop privacy 2009 Mar 23, 12:58Details on a particular browser exploit and how its been resolved in IE8. "One approach they presented allowed attackers to use .NET framework DLL's to allocate executable pages of memory at
predictable locations within the iexplore.exe process. They were then able to demonstrate how .NET behavior could be combined with a separate exploitable memory corruption vulnerability to run
arbitrary code."
 security ie8 ie browser hack via:ericlaw
security ie8 ie browser hack via:ericlaw 2009 Mar 23, 11:06The HTML5 spec tells us how it is in the real world for URLs: "This specification defines various algorithms for dealing with Web addresses intended for use by HTML user agents. For historical
reaons, in order to be compatible with existing Web content HTML user agents need to implement a number of processes not defined by the URI and IRI specifications [RFC3986], [RFC3987]."
 html html5 url uri reference w3c
html html5 url uri reference w3c
 I've made a QR Encode accelerator around Google Chart's QR code generator. QR codes are 2D bar-codes that can store (among other things) URLs and have good support on mobile
phones. The accelerator I've written lets you generate a QR code for a selected link and view it in the preview window. In combination with the ZXing
bar-code scanner app for my Android cellphone, its easy for me to right click on a link in IE8 on my desktop PC, hover over the QR Encode accelerator to have the link's associated QR code
displayed, and then with my phone read that QR code to open my phone's browser to the URL contained inside. Its much easier to browse around in the comfort of my desktop and only send particular
URLs to my cellphone as necessary.
I've made a QR Encode accelerator around Google Chart's QR code generator. QR codes are 2D bar-codes that can store (among other things) URLs and have good support on mobile
phones. The accelerator I've written lets you generate a QR code for a selected link and view it in the preview window. In combination with the ZXing
bar-code scanner app for my Android cellphone, its easy for me to right click on a link in IE8 on my desktop PC, hover over the QR Encode accelerator to have the link's associated QR code
displayed, and then with my phone read that QR code to open my phone's browser to the URL contained inside. Its much easier to browse around in the comfort of my desktop and only send particular
URLs to my cellphone as necessary.
 A while ago I promised to say how an xsltproc Meddler script would be useful and the general answer is
its useful for hooking up a client application that wants data from the web in a particular XML format and the data is available on the web but in another XML format. The specific case for this
post is a Flickr Search service that includes IE8 Visual Search Suggestions. IE8
wants the Visual Search Suggestions XML format and Flickr gives out search data in their Flickr web API XML format.
A while ago I promised to say how an xsltproc Meddler script would be useful and the general answer is
its useful for hooking up a client application that wants data from the web in a particular XML format and the data is available on the web but in another XML format. The specific case for this
post is a Flickr Search service that includes IE8 Visual Search Suggestions. IE8
wants the Visual Search Suggestions XML format and Flickr gives out search data in their Flickr web API XML format.