 The weekend before last was Sarah's birthday and as part of
that, last weekend we took a trip to Victoria, BC. I've got a map of our trip locations and photos. Not all the
photos are on the map but they're all in the trip photo set on Flickr. It turns out there's a lot of tourist intended
activities right around our hotel which was in the inner harbor and downtown Victoria area. As such we didn't get a rental car and did a lot of walking.
The weekend before last was Sarah's birthday and as part of
that, last weekend we took a trip to Victoria, BC. I've got a map of our trip locations and photos. Not all the
photos are on the map but they're all in the trip photo set on Flickr. It turns out there's a lot of tourist intended
activities right around our hotel which was in the inner harbor and downtown Victoria area. As such we didn't get a rental car and did a lot of walking.
 On the first day we checked out the Royal British Columbia Museum which had
some interesting exhibits in it and the Undersea Garden which was interesting in that its like a floating aquarium but was a bit grimy. There was a group of Japanese tourists next to us during the
undersea show in which a diver behind the glass in the ocean would pick up and parade various animal life. The group all repeated the word starfish in unison after the show's narrator and one of
the tourists was very excited to see the diver bring over the octopus. The diver made the octopus wave to us while it desperately tried to get away.
On the first day we checked out the Royal British Columbia Museum which had
some interesting exhibits in it and the Undersea Garden which was interesting in that its like a floating aquarium but was a bit grimy. There was a group of Japanese tourists next to us during the
undersea show in which a diver behind the glass in the ocean would pick up and parade various animal life. The group all repeated the word starfish in unison after the show's narrator and one of
the tourists was very excited to see the diver bring over the octopus. The diver made the octopus wave to us while it desperately tried to get away.
 We flew in and out of the Victoria International Airport
which is a smaller sized airport. Although we needed our passports we didn't need to take off our shoes -- what convenience! The US dollar was just a bit worse than the Canadian dollar which was
also convenient. The weather was lovely while we were there and I only got slightly sun burned.
We flew in and out of the Victoria International Airport
which is a smaller sized airport. Although we needed our passports we didn't need to take off our shoes -- what convenience! The US dollar was just a bit worse than the Canadian dollar which was
also convenient. The weather was lovely while we were there and I only got slightly sun burned.
 I just installed vmcNetFlix which lets you watch your on demand NetFlix movies via your Vista Media Center or any Media Center
Extenders like the Xbox 360. It works well but fails poorly with some cryptic error messages and long timeouts. Be sure to get NetFlix on demand movies working in your browser before installing
this plugin. Once I did that everything worked very well.
I just installed vmcNetFlix which lets you watch your on demand NetFlix movies via your Vista Media Center or any Media Center
Extenders like the Xbox 360. It works well but fails poorly with some cryptic error messages and long timeouts. Be sure to get NetFlix on demand movies working in your browser before installing
this plugin. Once I did that everything worked very well.
To test it out I watched Ong-Bak: The Thai Warrior in which Ting must travel from his country village to Bangkok where he works with his cousin in the city to recover his village's stolen religious artifact. Its a mix of Perfect Strangers, Street Fighter and Pad-See Ew. Martial arts movies, like porn and video games, aren't required to have a strong plot but Ong-Bak has a fine plot line and enjoyable Thai martial arts. I saw the Tiger Knee in there several times. An enjoyable movie that reminded me of watching martial arts movies with my friends in high school.
When I woke up this morning for some reason I was thinking about Polytope Tetris, my N-D Tetris game, and specifically generating Tetris pieces in various number of dimensions. When I first wrote PTT I thought that as the number of dimensions increased you could end up with an infinite number of non-equivalent crazy Tetris pieces. However this morning I realized that because you only get four blocks per piece there are only a possible three joints in a single Tetris piece which means that you only need three dimensions to represent all possible distinct N-D Tetris pieces.
Below is the table of the various possible pieces per number of dimensions and sorted by the number of joints in the piece. Notice that the 'J' and 'L' become equivalent in 3D because you can rotate the 'J' through the third dimension to make it an 'L'. The same happens for 'S' and 'Z' in 3D, and 'S+' and 'Z+' in 4D.
| Joints | Name | 1D | 2D | 3D | + |
|---|---|---|---|---|---|
| 1 | I |

|

|

|

|
| 2 | J |
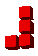
|
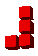
|
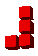
|
|
| L |
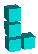
|
||||
| 3 | O |
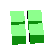
|
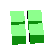
|
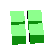
|
|
| T |

|

|

|
||
| S |

|

|

|
||
| Z |
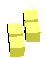
|
||||
| T+ |

|

|
|||
| S+ |

|

|
|||
| Z+ |

|
||||
| Total | 1 | 7 | 8 | 7 |
As a consequence of not realizing there's a finite and small number of N-D Tetris pieces, I wrote code that would randomly generate pieces for a specified number of dimensions by wandering through Tetris space. This consists of first marking the current spot, then randomly picking a direction (a dimension and either forward or backward), going in that direction until hitting a previously unvisited spot and repeating until four spots are marked, forming a Tetris piece. However this morning I realized that continuing in the same direction until reaching am unvisited spot means I can't generate the 'T+' piece. I think the better way to go is keep the list of all possible pieces, pick one randomly, and rotate it randomly through the available dimensions. Doing this will also allow me to give distinct pieces their own specific color (like the classic Tetris games do) rather than picking the color randomly like I do now.
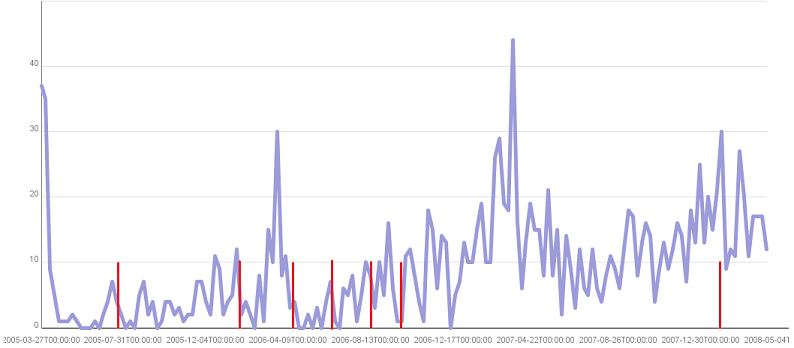
While re-reading Cryptonomicon I thought about what kind of information I'm leaking by posting links on Delicious. At work I don't post any Intranet websites for fear of revealing anything but I wondered if not posting would reveal anything. For instance, if I'm particularly busy at work might I post less indicating something about the state of the things I work on? I got an archive of my Delicious posts via the Delicious API and then ran it through a tool I made to create a couple of tables which I've graphed on Many Eyes


![[The cover of Cryptonomicon]](http://images.amazon.com/images/P/0380788624.01._SX140_SCLZZZZZZZ_.jpg)
![[The cover of Quicksilver]](http://images.amazon.com/images/P/0060593083.01._SX140_SCLZZZZZZZ_.jpg)
![[The cover of The Confusion]](http://images.amazon.com/images/P/0060733357.01._SX140_SCLZZZZZZZ_.jpg)
![[The cover of The System of the World]](http://images.amazon.com/images/P/0060750863.01._SX140_SCLZZZZZZZ_.jpg)
I've finally finished the Baroque Cycle, a historical fiction series set in the 17th and 18th centuries by Neal Stephenson whose work I always enjoy. There were often delays where I'd forget about the books until I had to take plane somewhere, or get discouraged reading about the character's thoughts on economics, or have difficulty finding the next volume, or become more engrossed in other books, projects or video games, and leave the Baroque Cycle books untouched for many months at a time. Consequently, my reading of this series has, I'm ashamed to say, spanned years. After finishing some books which I enjoy I end up hungry for just a bit more to read. For this series I don't need a bit more to read, I'm done with that, but I do want a badge or maybe a medal. Or barring that, college credit in European History and Macro Economics. I can recommend this book to anyone who has enjoyed Neal Stephenson's other work and has a few years of free time to kill.
 Last weekend after Saul and Ciera's wedding, I drove up to Pat, Grib, and Jesse's
house to which I hadn't previously been. I got in late and they'd just finished a UFC party. The next day Grib had to travel for work but the rest of us met Scott and Nicole, Jesse's girlfriend at
a place for breakfast. After that we went back to their place for some Rock Band which I hadn't played previously and Pat took the opportunity to show off his real life musical skills on the banjo.
Last weekend after Saul and Ciera's wedding, I drove up to Pat, Grib, and Jesse's
house to which I hadn't previously been. I got in late and they'd just finished a UFC party. The next day Grib had to travel for work but the rest of us met Scott and Nicole, Jesse's girlfriend at
a place for breakfast. After that we went back to their place for some Rock Band which I hadn't played previously and Pat took the opportunity to show off his real life musical skills on the banjo.
 This weekend, Jesse and Nicole are up visiting Seattle. On Friday, Sarah and I met up with them at the BluWater Bistro in Seattle which sits right on Lake Union. The view was nice although difficult to see from our table and overall I like the sister
restaurant in Kirkland better. They were both short visits but it was fun to see people again.
This weekend, Jesse and Nicole are up visiting Seattle. On Friday, Sarah and I met up with them at the BluWater Bistro in Seattle which sits right on Lake Union. The view was nice although difficult to see from our table and overall I like the sister
restaurant in Kirkland better. They were both short visits but it was fun to see people again.
 Last weekend while Sarah was up in Canada for a spa weekend with her sister and her sister's other bridesmaids, I went to Saul and Ciera's
wedding in Three Rivers, California near Sequoia National Park. I flew into Fresno picked up a rental car and my GPS device navigated me to a restaurant with the wedding location no where in sight.
"No problem," I thought, "I'll just call someone with an Internet connection and..." I had no cell reception. What did people do before GPS, Internet, and cell phones?
Last weekend while Sarah was up in Canada for a spa weekend with her sister and her sister's other bridesmaids, I went to Saul and Ciera's
wedding in Three Rivers, California near Sequoia National Park. I flew into Fresno picked up a rental car and my GPS device navigated me to a restaurant with the wedding location no where in sight.
"No problem," I thought, "I'll just call someone with an Internet connection and..." I had no cell reception. What did people do before GPS, Internet, and cell phones?
 A waitress in the restaurant pointed me down the road a bit to the wedding location which was outside overlooking a
river. Their wedding cake was made up like a mountain with two backpacks at the top and rope hanging down. Ciera's father married them and the ceremony was lovely. The music after included Code Monkey to which all the nerds were forced to get up and awkwardly dance.
A waitress in the restaurant pointed me down the road a bit to the wedding location which was outside overlooking a
river. Their wedding cake was made up like a mountain with two backpacks at the top and rope hanging down. Ciera's father married them and the ceremony was lovely. The music after included Code Monkey to which all the nerds were forced to get up and awkwardly dance.
 Besides getting to see Ciera and Saul who I hadn't seen in quite a while, I got to see Daniil and Val, Vlad, and Nathaniel. Since
last I saw Daniil and Val they had a child, Katie who is very cute and in whom I can see a lot of family resemblance. The always hilarious Vlad,
Daniil's brother, was there as well with his wife who I got to meet. Nathaniel, my manager from Vizolutions was there and I don't know if I've seen him since I moved to Washington. It was fun to
see him and meet his girlfriend who was kind enough to donate her extra male to male mini-phono cord so I could listen to my Zune in the rental car stereo on the drive back.
Besides getting to see Ciera and Saul who I hadn't seen in quite a while, I got to see Daniil and Val, Vlad, and Nathaniel. Since
last I saw Daniil and Val they had a child, Katie who is very cute and in whom I can see a lot of family resemblance. The always hilarious Vlad,
Daniil's brother, was there as well with his wife who I got to meet. Nathaniel, my manager from Vizolutions was there and I don't know if I've seen him since I moved to Washington. It was fun to
see him and meet his girlfriend who was kind enough to donate her extra male to male mini-phono cord so I could listen to my Zune in the rental car stereo on the drive back.
![['Neverending story' by Alexandre Duret-Lutz. A framed photo of books with the droste effect applied. Licensed under creative commons.]](http://farm1.static.flickr.com/90/252757784_3de44cbeb4_m_d.jpg) Information about URI Fragments, the portion of URIs
that follow the '#' at the end and that are used to navigate within a document, is scattered throughout various documents which I usually have to hunt down. Instead I'll link to them all here.
Information about URI Fragments, the portion of URIs
that follow the '#' at the end and that are used to navigate within a document, is scattered throughout various documents which I usually have to hunt down. Instead I'll link to them all here.
Definitions. Fragments are defined in the URI RFC which states that they're used to identify a secondary resource that is related to the primary resource identified by the URI as a subset of the primary, a view of the primary, or some other resource described by the primary. The interpretation of a fragment is based on the mime type of the primary resource. Tim Berners-Lee notes that determining fragment meaning from mime type is a problem because a single URI may contain a single fragment, however over HTTP a single URI can result in the same logical resource represented in different mime types. So there's one fragment but multiple mime types and so multiple interpretations of the one fragment. The URI RFC says that if an author has a single resource available in multiple mime types then the author must ensure that the various representations of a single resource must all resolve fragments to the same logical secondary resource. Depending on which mime types you're dealing with this is either not easy or not possible.
HTTP. In HTTP when URIs are used, the fragment is not included. The General Syntax section of the HTTP standard says it uses the definitions of 'URI-reference' (which includes the fragment), 'absoluteURI', and 'relativeURI' (which don't include the fragment) from the URI RFC. However, the 'URI-reference' term doesn't actually appear in the BNF for the protocol. Accordingly the headers like 'Request-URI', 'Content-Location', 'Location', and 'Referer' which include URIs are defined with 'absoluteURI' or 'relativeURI' and don't include the fragment. This is in keeping with the original fragment definition which says that the fragment is used as a view of the original resource and consequently only needed for resolution on the client. Additionally, the URI RFC explicitly notes that not including the fragment is a privacy feature such that page authors won't be able to stop clients from viewing whatever fragments the client chooses. This seems like an odd claim given that if the author wanted to selectively restrict access to portions of documents there are other options for them like breaking out the parts of a single resource to which the author wishes to restrict access into separate resources.
HTML. In HTML, the HTML mime type RFC defines HTML's fragment use which consists of fragments referring to elements with a corresponding 'id' attribute or one of a particular set of elements with a corresponding 'name' attribute. The HTML spec discusses fragment use additionally noting that the names and ids must be unique in the document and that they must consist of only US-ASCII characters. The ID and NAME attributes are further restricted in section 6 to only consist of alphanumerics, the hyphen, period, colon, and underscore. This is a subset of the characters allowed in the URI fragment so no encoding is discussed since technically its not needed. However, practically speaking, browsers like FireFox and Internet Explorer allow for names and ids containing characters outside of the defined set including characters that must be percent-encoded to appear in a URI fragment. The interpretation of percent-encoded characters in fragments for HTML documents is not consistent across browsers (or in some cases within the same browser) especially for the percent-encoded percent.
Text. Text/plain recently got a fragment definition that allows fragments to refer to particular lines or characters within a text document. The scheme no longer includes regular expressions, which disappointed me at first, but in retrospect is probably good idea for increasing the adoption of this fragment scheme and for avoiding the potential for ubiquitous DoS via regex. One of the authors also notes this on his blog. I look forward to the day when this scheme is widely implemented.
XML. XML has the XPointer framework to define its fragment structure as noted by the XML mime type definition. XPointer consists of a general scheme that contains subschemes that identify a subset of an XML document. Its too bad such a thing wasn't adopted for URI fragments in general to solve the problem of a single resource with multiple mime type representations. I wrote more about XPointer when I worked on hacking XPointer into IE.
SVG and MPEG. Through the Media Fragments Working Group I found a couple more fragment scheme definitions. SVG's fragment scheme is defined in the SVG documentation and looks similar to XML's. MPEG has one defined but I could only find it as an ISO document "Text of ISO/IEC FCD 21000-17 MPEG-12 FID" and not as an RFC which is a little disturbing.
AJAX. AJAX websites have used fragments as an escape hatch for two issues that I've seen. The first is getting a unique URL for versions of a page that are produced on the client by script. The fragment may be changed by script without forcing the page to reload. This goes outside the rules of the standards by using HTML fragments in a fashion not called out by the HTML spec. but it does seem to be inline with the spirit of the fragment in that it is a subview of the original resource and interpretted client side. The other hack-ier use of the fragment in AJAX is for cross domain communication. The basic idea is that different frames or windows may not communicate in normal fashions if they have different domains but they can view each other's URLs and accordingly can change their own fragments in order to send a message out to those who know where to look. IMO this is not inline with the spirit of the fragment but is rather a cool hack.
 It was warm and lovely out this past Saturday and Sarah I and went to a
new place for lunch, then to Kelsey Creek Park, and then out for Jane's birthday. We ate at Cafe
Pirouette which serves crepes and is done up with French decorations reminding me of my parent's house. We got in for just the end of lunch and saw the second to last customers, a gaggle of
older ladies leaving. I felt a little out of place with my "Longhorn [heart] RSS" t-shirt on. The food was good and in larger portions that I expected.
It was warm and lovely out this past Saturday and Sarah I and went to a
new place for lunch, then to Kelsey Creek Park, and then out for Jane's birthday. We ate at Cafe
Pirouette which serves crepes and is done up with French decorations reminding me of my parent's house. We got in for just the end of lunch and saw the second to last customers, a gaggle of
older ladies leaving. I felt a little out of place with my "Longhorn [heart] RSS" t-shirt on. The food was good and in larger portions that I expected.
 After that we went to Kelsey Creek Park and Farm. The park is hidden at the end of a quiet neighborhood, starts out with some tables and children's jungle gym
equipment, then there's a farm which includes a petting zoo, followed by many little trails going off into the forrest. There weren't too many animals out and the ones we did see didn't seem to
expect or want the sun and warm weather. We followed one of the trails for a bit and turned back before getting sun burned. You can see
my weekend photos mapped out on Live Maps.
After that we went to Kelsey Creek Park and Farm. The park is hidden at the end of a quiet neighborhood, starts out with some tables and children's jungle gym
equipment, then there's a farm which includes a petting zoo, followed by many little trails going off into the forrest. There weren't too many animals out and the ones we did see didn't seem to
expect or want the sun and warm weather. We followed one of the trails for a bit and turned back before getting sun burned. You can see
my weekend photos mapped out on Live Maps.
That night we went out with some friends for Jane's birthday. Eric was just back from the RSA conference and we met Jane and Eric and others at Palace Kitchen in Seattle located immediately adjascent to the monorail's route. The weather was still good so they left the large windows open through twilight and every so often you'd see the monorail pass by.
For Encode-O-Matic, my encoding tool written in C#, I had to figure out the appropriate DllImport declarations to use IDN Win32 functions which was a pain. To spare others that pain here's the two files CharacterSetEncoding.cs and NationalLanguageSupportUtilities.cs that declare the DllImports for IdnToUnicode, IdnToAscii, NormalizeString, MultiByteToWideChar, and WideCharToMultiByte.
 More of my thoughts have been stolen: In my
previous job the customer wanted a progress bar displayed while information was copied off of proprietary hardware, during which the software didn't get any indication of progress until the copy
was finished. I joked (mostly) that we could display a progress bar that continuously slows down and never quite reaches the end until we know we're done getting info from the hardware. The amount
of progress would be a function of time where as time approaches infinity, progress approaches a value of at most 100 percent.
More of my thoughts have been stolen: In my
previous job the customer wanted a progress bar displayed while information was copied off of proprietary hardware, during which the software didn't get any indication of progress until the copy
was finished. I joked (mostly) that we could display a progress bar that continuously slows down and never quite reaches the end until we know we're done getting info from the hardware. The amount
of progress would be a function of time where as time approaches infinity, progress approaches a value of at most 100 percent.
This is similar to Zeno's Paradox which says you can't cross a room because to do so first you must cross half the room, then you must cross half the remaining distance, then half the remaining again, and so on which means you must take an infinite number of steps. There's also an old joke inspired by Zeno's Paradox. The joke is the prototypical engineering vs sciences joke and is moderately humorous, but I think the fact that Wolfram has an interactive applet demonstrating the joke is funnier than the joke itself.
I recently found Lou Franco's blog post "Using Zeno's Paradox For Progress Bars" which covers the same concept as Zeno's Progress Bar but with real code. Apparently Lou wasn't making a joke and actually used this progress bar in an application. A progress bar that doesn't accurately represent progress seems dishonest. In cases like the Vista Defrag where the software can't make a reasonable guess about how long a process will take the software shouldn't display a progress bar.
Similarly a paper by Chris Harrison "Rethinking the Progress Bar" suggests that if a progress bar speeds up towards the end the user will perceive the operation as taking less time. The paper is interesting, but as in the previous case, I'd rather have progress accurately represented even if it means the user doesn't perceive the operation as being as fast.
Update: I should be clearer about Lou's post. He was actually making a practical and implementable suggestion as to how to handle the case of displaying progress when you have some idea of how long it will take but no indications of progress, whereas my suggestion is impractical and more of a joke concerning displaying progress with no indication of progress nor a general idea of how long it will take.