The weekend before last I saw Dark Knight with some friends from work and then we all ate at Z'Tejas after. Like everyone has said and as the name implies Dark Knight is... dark. Dark Knight was a little over the top at times as compared to Batman Begins but I really enjoyed it. Two times during the movie I thought it had ended but I was wrong. The Joker is both frightening (Cringe inducing line "Wanna know how I got these scars?") and humorous ("Where is Harvey Dent? ... You know where Harvey is? You know who he is?", as well as the pencil magic trick). I can certainly recommend it to anyone who enjoyed Batman Begins. The previews included Burn After Reading a new Coen Brother's comedy that I look forward to, and Quantum of Solace which hopefully does the same thing Dark Knight has, keep up the new direction on the refreshed franchise.
 This past
weekend Sarah and I went to a Mariners baseball game. I think this is the first MLB baseball game I've seen in person. Sarah's company gave out tickets for the game and the use of a suite. Its a
room half way up the stadium with comfortable chairs, a mini-fridge built-in to the marble counter-topped center table, and a big flat screen television with the game on it. I suppose that's in
case you don't want to turn to the right and sit at the window, or walk out onto the balcony which features three rows of comfy chairs overlooking the field. Anyway there was free food and drinks
and I met some of the people Sarah works with.
This past
weekend Sarah and I went to a Mariners baseball game. I think this is the first MLB baseball game I've seen in person. Sarah's company gave out tickets for the game and the use of a suite. Its a
room half way up the stadium with comfortable chairs, a mini-fridge built-in to the marble counter-topped center table, and a big flat screen television with the game on it. I suppose that's in
case you don't want to turn to the right and sit at the window, or walk out onto the balcony which features three rows of comfy chairs overlooking the field. Anyway there was free food and drinks
and I met some of the people Sarah works with.
 Saturday we went to Kirkland Uncorked,
a wine tasting festival near our home. We took the bus and after finding the correct one (they really should have different numbers for buses that are on the same route but traveling in different
directions) made it to the festival. Unfortunately I don't remember any of the names of the wines just which ones I enjoyed by order. Recalling that I enjoyed the first one I had and the second to
last one, doesn't really help me find them again. There were local artists who had setup booths and Sarah got
a lovely necklace. After that we ate at Cactus which, because it was such a lovely day, had all its windows and doors open.
Saturday we went to Kirkland Uncorked,
a wine tasting festival near our home. We took the bus and after finding the correct one (they really should have different numbers for buses that are on the same route but traveling in different
directions) made it to the festival. Unfortunately I don't remember any of the names of the wines just which ones I enjoyed by order. Recalling that I enjoyed the first one I had and the second to
last one, doesn't really help me find them again. There were local artists who had setup booths and Sarah got
a lovely necklace. After that we ate at Cactus which, because it was such a lovely day, had all its windows and doors open.
Sunday was quieter. A few household chores and plenty of GTA4. I almost got the One Man Army achievement but I found that after four minutes with six stars I eventually dropped back down to three stars without realizing it.



I want to once again profess my love for the Wii's Virtual Console. Sarah and I recently finished playing through the first three Zelda games. Although I'd played a bit of the first two I never had a Nintendo as a kid and so unlike Sarah this was my first time completely playing through Zelda I & II. What people say about Zelda II is true... its all so true. And on the flip side I have fond memories of beating the third Zelda game which Sarah hadn't played.
In hilarious Zelda related news, a friend from work's husband posted the following blog post concerning their son named Link.
My GPS was stolen last night or this morning and I'm missing it already. For instance when I drove to Novus glass repair to get my front passenger window replaced I drove down the wrong road for a while.
When I got out of my apartment this morning there was a police car sitting in my parking lot and the officer asked me: "David? ... What'd you leave in your car?". My face must have changed a lot when I had the following sequence of realizations: (a) a police officer is asking for me by name, (b) I'm not in trouble, (c) my car must have been burgled, and (d) my GPS must be stolen.
The officer was waiting outside my complex because someone had reported my car's broken window to the police in the morning. The officer was very courteous and upon taking my date of birth noted that we were born on exactly the same day. The window's safety glass was shattered and lying in tons of tiny pieces all over the passenger seat, my glove box was open and the middle armrest where I keep my CDs was open. Nothing appears to be missing other than the GPS, the GPS power cable, and the GPS dash mount. Adding insult to theft, the their scattered my CDs throughout my car and didn't take any of them, insulting my taste in music.
My car's window should be repaired now and hopefully the rain that came in through the broken window until I covered it with plastic bags (classy!) didn't do any permanent damage.
When I woke up this morning for some reason I was thinking about Polytope Tetris, my N-D Tetris game, and specifically generating Tetris pieces in various number of dimensions. When I first wrote PTT I thought that as the number of dimensions increased you could end up with an infinite number of non-equivalent crazy Tetris pieces. However this morning I realized that because you only get four blocks per piece there are only a possible three joints in a single Tetris piece which means that you only need three dimensions to represent all possible distinct N-D Tetris pieces.
Below is the table of the various possible pieces per number of dimensions and sorted by the number of joints in the piece. Notice that the 'J' and 'L' become equivalent in 3D because you can rotate the 'J' through the third dimension to make it an 'L'. The same happens for 'S' and 'Z' in 3D, and 'S+' and 'Z+' in 4D.
| Joints | Name | 1D | 2D | 3D | + |
|---|---|---|---|---|---|
| 1 | I |

|

|

|

|
| 2 | J |
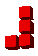
|
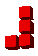
|
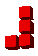
|
|
| L |
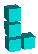
|
||||
| 3 | O |
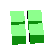
|
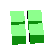
|
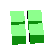
|
|
| T |

|

|

|
||
| S |

|

|

|
||
| Z |
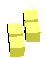
|
||||
| T+ |

|

|
|||
| S+ |

|

|
|||
| Z+ |

|
||||
| Total | 1 | 7 | 8 | 7 |
As a consequence of not realizing there's a finite and small number of N-D Tetris pieces, I wrote code that would randomly generate pieces for a specified number of dimensions by wandering through Tetris space. This consists of first marking the current spot, then randomly picking a direction (a dimension and either forward or backward), going in that direction until hitting a previously unvisited spot and repeating until four spots are marked, forming a Tetris piece. However this morning I realized that continuing in the same direction until reaching am unvisited spot means I can't generate the 'T+' piece. I think the better way to go is keep the list of all possible pieces, pick one randomly, and rotate it randomly through the available dimensions. Doing this will also allow me to give distinct pieces their own specific color (like the classic Tetris games do) rather than picking the color randomly like I do now.
![['Neverending story' by Alexandre Duret-Lutz. A framed photo of books with the droste effect applied. Licensed under creative commons.]](http://farm1.static.flickr.com/90/252757784_3de44cbeb4_m_d.jpg) Information about URI Fragments, the portion of URIs
that follow the '#' at the end and that are used to navigate within a document, is scattered throughout various documents which I usually have to hunt down. Instead I'll link to them all here.
Information about URI Fragments, the portion of URIs
that follow the '#' at the end and that are used to navigate within a document, is scattered throughout various documents which I usually have to hunt down. Instead I'll link to them all here.
Definitions. Fragments are defined in the URI RFC which states that they're used to identify a secondary resource that is related to the primary resource identified by the URI as a subset of the primary, a view of the primary, or some other resource described by the primary. The interpretation of a fragment is based on the mime type of the primary resource. Tim Berners-Lee notes that determining fragment meaning from mime type is a problem because a single URI may contain a single fragment, however over HTTP a single URI can result in the same logical resource represented in different mime types. So there's one fragment but multiple mime types and so multiple interpretations of the one fragment. The URI RFC says that if an author has a single resource available in multiple mime types then the author must ensure that the various representations of a single resource must all resolve fragments to the same logical secondary resource. Depending on which mime types you're dealing with this is either not easy or not possible.
HTTP. In HTTP when URIs are used, the fragment is not included. The General Syntax section of the HTTP standard says it uses the definitions of 'URI-reference' (which includes the fragment), 'absoluteURI', and 'relativeURI' (which don't include the fragment) from the URI RFC. However, the 'URI-reference' term doesn't actually appear in the BNF for the protocol. Accordingly the headers like 'Request-URI', 'Content-Location', 'Location', and 'Referer' which include URIs are defined with 'absoluteURI' or 'relativeURI' and don't include the fragment. This is in keeping with the original fragment definition which says that the fragment is used as a view of the original resource and consequently only needed for resolution on the client. Additionally, the URI RFC explicitly notes that not including the fragment is a privacy feature such that page authors won't be able to stop clients from viewing whatever fragments the client chooses. This seems like an odd claim given that if the author wanted to selectively restrict access to portions of documents there are other options for them like breaking out the parts of a single resource to which the author wishes to restrict access into separate resources.
HTML. In HTML, the HTML mime type RFC defines HTML's fragment use which consists of fragments referring to elements with a corresponding 'id' attribute or one of a particular set of elements with a corresponding 'name' attribute. The HTML spec discusses fragment use additionally noting that the names and ids must be unique in the document and that they must consist of only US-ASCII characters. The ID and NAME attributes are further restricted in section 6 to only consist of alphanumerics, the hyphen, period, colon, and underscore. This is a subset of the characters allowed in the URI fragment so no encoding is discussed since technically its not needed. However, practically speaking, browsers like FireFox and Internet Explorer allow for names and ids containing characters outside of the defined set including characters that must be percent-encoded to appear in a URI fragment. The interpretation of percent-encoded characters in fragments for HTML documents is not consistent across browsers (or in some cases within the same browser) especially for the percent-encoded percent.
Text. Text/plain recently got a fragment definition that allows fragments to refer to particular lines or characters within a text document. The scheme no longer includes regular expressions, which disappointed me at first, but in retrospect is probably good idea for increasing the adoption of this fragment scheme and for avoiding the potential for ubiquitous DoS via regex. One of the authors also notes this on his blog. I look forward to the day when this scheme is widely implemented.
XML. XML has the XPointer framework to define its fragment structure as noted by the XML mime type definition. XPointer consists of a general scheme that contains subschemes that identify a subset of an XML document. Its too bad such a thing wasn't adopted for URI fragments in general to solve the problem of a single resource with multiple mime type representations. I wrote more about XPointer when I worked on hacking XPointer into IE.
SVG and MPEG. Through the Media Fragments Working Group I found a couple more fragment scheme definitions. SVG's fragment scheme is defined in the SVG documentation and looks similar to XML's. MPEG has one defined but I could only find it as an ISO document "Text of ISO/IEC FCD 21000-17 MPEG-12 FID" and not as an RFC which is a little disturbing.
AJAX. AJAX websites have used fragments as an escape hatch for two issues that I've seen. The first is getting a unique URL for versions of a page that are produced on the client by script. The fragment may be changed by script without forcing the page to reload. This goes outside the rules of the standards by using HTML fragments in a fashion not called out by the HTML spec. but it does seem to be inline with the spirit of the fragment in that it is a subview of the original resource and interpretted client side. The other hack-ier use of the fragment in AJAX is for cross domain communication. The basic idea is that different frames or windows may not communicate in normal fashions if they have different domains but they can view each other's URLs and accordingly can change their own fragments in order to send a message out to those who know where to look. IMO this is not inline with the spirit of the fragment but is rather a cool hack.

 With the new features of IE8 there's several easy ways to integrate Gmail, Google's web mail service, for mail composition, searching, and monitoring that I enjoy using.
With the new features of IE8 there's several easy ways to integrate Gmail, Google's web mail service, for mail composition, searching, and monitoring that I enjoy using.
 At the grocery store the other day Sarah and I attempted to find shallot for a recipe, but I can't
tell the difference between shallot, sweet onions, yellow onions, etc. etc. We found something that we decided was the closest we'd find in the store and I believe we picked correctly because at
checkout the cashier rang it up as shallot.
At the grocery store the other day Sarah and I attempted to find shallot for a recipe, but I can't
tell the difference between shallot, sweet onions, yellow onions, etc. etc. We found something that we decided was the closest we'd find in the store and I believe we picked correctly because at
checkout the cashier rang it up as shallot.
 I think this could be
a practical problem that the 20q Pocket Mind Reader should be able to solve: obtain the name of an unidentified object. When we got home
I decided to test the 20q Pocket Mind Reader on shallot. Unfortunately, it told me I had an onion, but I think if these were designed for identifying unknown objects based solely on information you
can obtain by looking at it, rather than requiring knowledge of seeds, where it grows, etc. it would do better. Or I could just ask someone who works at the grocery store.
I think this could be
a practical problem that the 20q Pocket Mind Reader should be able to solve: obtain the name of an unidentified object. When we got home
I decided to test the 20q Pocket Mind Reader on shallot. Unfortunately, it told me I had an onion, but I think if these were designed for identifying unknown objects based solely on information you
can obtain by looking at it, rather than requiring knowledge of seeds, where it grows, etc. it would do better. Or I could just ask someone who works at the grocery store.
 I signed up for the pre-release beta and purchased a Chumby last year. Chumby looks like a cousin to a GPS
unit. Its similar in size with a touch screen, but has WiFi, accelerometers, and is pillow like on the sides that aren't a screen. In practice its like an Internet alarm clock that shows you photos
and videos off the Web. Its hackable in that Chumby Industries tells you about the various ways to run your own stuff on the Chumby, modifying the boot sequence (it runs Linux), turning on sshd,
etc, etc. The Chumby forum too has lots of info from folks who have found interesting hacks for the device.
I signed up for the pre-release beta and purchased a Chumby last year. Chumby looks like a cousin to a GPS
unit. Its similar in size with a touch screen, but has WiFi, accelerometers, and is pillow like on the sides that aren't a screen. In practice its like an Internet alarm clock that shows you photos
and videos off the Web. Its hackable in that Chumby Industries tells you about the various ways to run your own stuff on the Chumby, modifying the boot sequence (it runs Linux), turning on sshd,
etc, etc. The Chumby forum too has lots of info from folks who have found interesting hacks for the device.
When you turn on the Chumby it downloads and runs the latest version of the Chumby software which lets you set alarms, play music, and display Flash widgets. The Chumby website lets anyone upload their own Flash widgets to share with the community. I tried my hand at creating one using Adobe's free Flash creation SDK but I don't know Flash and didn't have the patience to learn.
Currently my Chumby is set to wake me up at 8am on weekdays with music from ShoutCast and then displays traffic and weather. At 10am everyday it switches to showing me a slide-show of LolCats. At 11pm it switches to night mode where it displays the time in dark grey text on a black background at a reduced light level so as not to disturb me while I sleep.
I like the Chumby but I have two complaints. The first is that it forces me to learn flash in order to create anything cool rather than having a built-in Web browser or depending on a more Web friendly technology. The second complaint is about its name. At first I thought the name was stupid in a kind of silly way, but now that I'm used to the name it sounds vaguely dirty.
 I got a FlickrMail from Emma J. Williams a bit ago saying that they wanted to
use two of my photos in their Schmap San Francisco Guide online travel guide. So now you can see two of my vacation photos on the Westfield San Francisco Shopping Center Schmap page and the Hotel Diva Schmap page.
I got a FlickrMail from Emma J. Williams a bit ago saying that they wanted to
use two of my photos in their Schmap San Francisco Guide online travel guide. So now you can see two of my vacation photos on the Westfield San Francisco Shopping Center Schmap page and the Hotel Diva Schmap page.
 I think its wonderful that digital cameras are at
the point where I really don't have to know much about their workings to produce a photo that's reasonable looking. And its thanks to Flickr and searchable tags that Schmap could find my photos.
Since my photos on Flickr are all licensed under a Creative Commons license named Attribution-Noncommercial-No Derivative Works
2.0 Generic which only applies to non-commercial uses, Schmap, which is advertisement supported, kindly asked me if they could use my photos. I agreed to their license which was human readable
and included wonderful stuff like I get in place attribution and the license is only applicable while Schmap makes their guide freely available online.
I think its wonderful that digital cameras are at
the point where I really don't have to know much about their workings to produce a photo that's reasonable looking. And its thanks to Flickr and searchable tags that Schmap could find my photos.
Since my photos on Flickr are all licensed under a Creative Commons license named Attribution-Noncommercial-No Derivative Works
2.0 Generic which only applies to non-commercial uses, Schmap, which is advertisement supported, kindly asked me if they could use my photos. I agreed to their license which was human readable
and included wonderful stuff like I get in place attribution and the license is only applicable while Schmap makes their guide freely available online.
Previously I've only heard of folks having their flickr photos used without their permission so I'm glad to know that's not always the case. Or perhaps this is just Schmap's clever method of getting me to blog about them.