2010 Jul 8, 11:07"!undef [macro]" to undefine a macro...
 microsoft reference programming technical msdn build
microsoft reference programming technical msdn build 2010 Jul 5, 8:38"This way the player appears to control their own character without any latency, and provided that the client and server character simulation code is deterministic – giving exactly the same result
for the same inputs on the client and server – it is rarely corrected."
 network programming game technical quake history
network programming game technical quake history 2010 Jul 5, 4:23Cross-site scripting attack on YouTube over the weekend: "That turned out to be as simple as using two script tags in a row (<script><script>fun scripting stuff goes here!), as noted by
F-Secure researcher Mikko H. Hypponen on Twitter—the first of the two tags would get stripped, and the second was allowed through."
 technical youtube security cross-site-scripting javascript
technical youtube security cross-site-scripting javascript 2010 Jul 1, 10:51"Sometimes it’s hard to judge whether an engineering effort has been successful or not. It can take years for an idea to catch on, to go from being the butt of jokes to becoming an international
imperative (IPv6). Uniform Resource Names (URNs), which are part of the Uniform Resource Identifier (URI) family, are conceptually at least as old as IPv6. While not figuring in international
directives for deployment, they-and the technology engineered to resolve them-are still going concerns."
 ietf urn uri history technical internet url
ietf urn uri history technical internet url 2010 Jul 1, 3:33"By charting the production of new books, new music albums, and new feature films over the last decade, the authors tried to see whether creative output went up or down in correlation with
file-sharing." They find that creative output is going up while piracy also increases. But this is correlation not causation. They can't say there wouldn't be more creative output with less piracy.
Regardless, still an interesting statistic.
 arstechnica copyright law economics ip piracy music technical
arstechnica copyright law economics ip piracy music technical 2010 Jun 29, 6:40A fan made Kings Quest sequel gets an official go-ahead: "After negotiations, the C&D [cease and desist] has been officially rescinded, and Phoenix Online has been granted a non-commercial
license to release The Silver Lining!"
 game legal law videogame kings-quest sierra technical
game legal law videogame kings-quest sierra technical 2010 Jun 25, 2:58"... all you need to do is specify the /W switch and the file or folder you want to overwrite—after you have already deleted it. cipher /W:C:\Path\To\Folder"
 technical cmd privacy security windows cipher delete
technical cmd privacy security windows cipher delete 2010 Jun 22, 1:49"The PowerGUI Visual Studio Extension adds PowerShell IntelliSense support to Visual Studio."
 technical powershell visual-studio microsoft programming shell ide
technical powershell visual-studio microsoft programming shell ide 2010 Jun 20, 2:05A more friendly summary of the Salmon Protocol -- the distributed commenting procotol. After telling Sarah I was reading about salmon, we watched the Salmon Dance video again.
 technical salmon protocol comment atom rss social reference
technical salmon protocol comment atom rss social reference 2010 Jun 20, 1:18Protocol for doing distributed commenting and implemented by Google Buzz! "This document defines a lightweight, robust, and secure protocol for sending unsolicited notifications — especially comments
and responses on syndicated feed content — to specified endpoints; along with rules to enable resulting content to itself be syndicated robustly and securely."
 comment blog atom rss google buzz salmon reference specification protocol syndication technical
comment blog atom rss google buzz salmon reference specification protocol syndication technical 2010 Jun 20, 1:16"This document specifies relation types for Web links, and defines a registry for them. It also defines the use of such links in HTTP headers with the Link header-field."
 html http rest url uri meta reference technical link ietf
html http rest url uri meta reference technical link ietf 2010 Jun 9, 3:31"A 'geo' URI identifies a physical location in a two- or three-dimensional coordinate reference system in a compact, simple, human-readable, and protocol-independent way."
 technical geo uri url ietf rfc standard
technical geo uri url ietf rfc standard 2010 Jun 7, 2:40Maps of where tourists vs locals take photos in major cities like New York, San Francisco, etc. based on geotagged photos on Flickr.
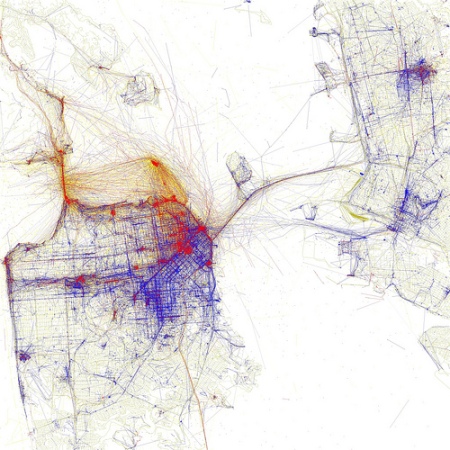
 geolocation geo geography map flickr photo tourist technical visualization
geolocation geo geography map flickr photo tourist technical visualization 2010 Jun 1, 6:46"Metalink describes download locations (mirrors), cryptographic hashes, and other information. Clients can transparently use this information to reliably transfer files."
 technical internet download web url xml metalink
technical internet download web url xml metalink 2010 May 27, 8:52Time to stock up on prepaid anonymous cell phones before its too late! Or just use the call encryption Android application...
 privacy security cellphone anonymous politics government technical
privacy security cellphone anonymous politics government technical

